Implementing Know Your Customer (KYC) processes is not only a way to assess customer risk and ensure a secure business environment but also a mandatory obligation to comply with Anti-Money Laundering (AML) requirements. Understanding applicable laws isn’t enough in today’s fast-progressing environment.
More industries, like MSBs and crypto exchanges, are being struck with stricter KYC requirements. But what exactly are they? In this blog post, we provide you with the basic 3 steps of KYC and tips on how to achieve and properly maintain KYC compliance.
What is Know Your Customer (KYC)?
KYC refers to Know Your Customer. It’s also known as Know Your Client, customer due diligence (CDD), or the process of identity verification. This process is designed to do a background check on customers before starting a business relationship with them. In other words, KYC verifies user identities to help you better understand who you’re dealing with.
Depending on the risk level, the KYC process occurs during the customer onboarding stage. Additionally, customers can be re-verified later during their cycle, especially in cases when their risk profile changes. Keep in mind that customers in this context can be both individuals and businesses.
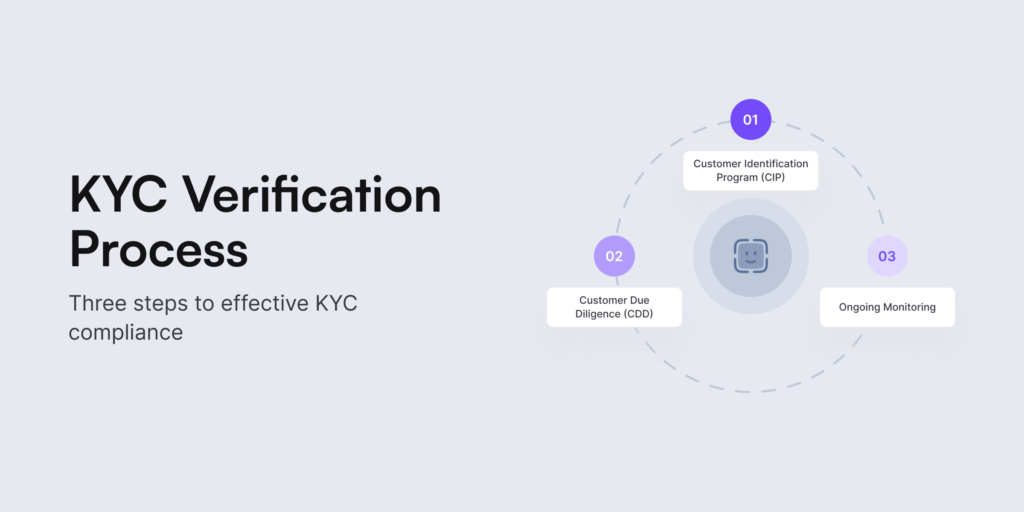
The fundamental rule for KYC involves three components:
- Establishing the customer’s identity.
- Understanding their background and customer activity while ensuring the legitimacy of their transactional behavior.
- Assessing further money laundering risks during ongoing monitoring.
Failure to follow primary obligations will result in an ineffective KYC program. Unfortunately, this scenario has severe consequences, such as sanctions, financial penalties, and damaged reputation.
The 3 Steps to KYC Compliance
The KYC process consists of three primary steps: CIP, CDD, and ongoing monitoring. We go through each step in more detail below:
1. Customer Identification Program (CIP)
The first phase in the KYC process is the Customer Identification Program (CIP). It revolves around collecting and validating customer information. In general, CIP refers to a set of procedures that a business is required to put in place and adhere to for the purpose of confirming the identity of its customers.
Typically, this means that customers must submit documents such as government-issued IDs, proof of address, and occasionally proof of income. Moreover, it’s essential for businesses to evaluate the risk associated with each customer. This assessment takes into account factors like the customer’s occupation, country of origin, and the type of transactions they engage in. Customers deemed high-risk demand additional scrutiny, which leads to the second step of KYC.
The primary objective of CIP programs is to verify that customers are indeed the individuals they claim to be. These programs play a crucial role in identifying and preventing occurrences of money laundering, identity theft, and various other types of fraud.
Related: What is the Difference Between CIP and KYC?
2. Customer Due Diligence (CDD)
Customer due diligence (CDD) involves a series of continuous procedures designed to evaluate customer risk. That’s why, after verifying a user’s identity, organizations must gather more information and conduct a deeper assessment of their profile through customer due diligence to detect any suspicious or risky behavior. This process is a fundamental aspect of KYC practices to help companies establish the trust of potential customers.
CDD has four key requirements:
- Identify and verify all customers or clients.
- Identify and verify all beneficial owners — individuals controlling 20% or more of the company).
- Understand the nature of customer relationships to establish customer risk profiles.
- Continuously monitor customer activities and transactions to detect and report any suspicious behavior.
Enhanced due diligence (EDD) is necessary for high-risk customers or accounts prone to unauthorized access or fraud. It involves gathering more information about such customers to understand their activities better and reduce the risk of fraud. To decide whether you need EDD, you should pay attention to the customer’s location, occupation, transactional behavior (value, frequency, and suspicious patterns), as well as the payment methods that they use.
Although some EDD requirements are defined by a country’s laws, similar to the overall KYC framework, companies have their own responsibility to assess risk and take actions to prevent wrongdoing by their customers.
Related: What is the Difference Between KYC and CDD?
3. Ongoing Monitoring
Ongoing monitoring, also sometimes referred to as continuous monitoring, is another vital component of your KYC processes. It involves the regular checking and verification of customer information to confirm ongoing compliance with regulatory standards. Ongoing monitoring’s goal is to help companies uncover any potential signs of suspicious or unlawful activities.
To put it simply, as customer information can change over time, ongoing monitoring in KYC compliance helps maintain the security of accounts and ensures that the organization remains compliant. Depending on the customer and your risk mitigation strategy, you should also keep an eye on various risk factors, including unusual or cross-border activities that fall outside the norm, sudden spikes, adverse media mentions, PEPs or sanctioned individuals. If the user is deemed unusual, you’ll need to file a Suspicious Activity Report (SAR).
Why Should You Pay Attention to KYC?
While KYC compliance isn’t the number one process that businesses like spending their money on, it’s a non-negotiable responsibility. Implementing proper KYC measures means that the business protects its customers with the highest security level in mind.
A perfect illustration of this is the healthcare industry, where patients’ data must be protected from cybercrime and other bad actors, for example, trying to get health insurance not in the best possible ways. Here, KYC has its own term, which is Know Your Patient (KYP). It serves as an essential safeguard for healthcare professionals to combat drug abuse, medical identity theft, and other fraudulent activities.
Another popular misconception about KYC is that it’s just another hassle for customers. If done right, KYC can actually benefit users without adding unnecessary friction. To put it simply, by establishing an effective identity verification process, you can demonstrate your commitment to transparency and the security of your users’ accounts. Furthermore, KYC serves as a preventive measure against various types of fraud, such as multiple account fraud and ATO fraud, which frequently occur in online marketplaces.
What Industries Need to Implement KYC?
There are many industries that require KYC verification. Each country and jurisdiction has different laws. Typically, sectors like banking, cryptocurrency, real estate, or iGaming require at least one form of identification, for example, a driver’s license, passport, social security card, or birth certificate. Most popular KYC methods include document verification or selfie identity verification, often combined with additional checks, like Proof of Address (PoA) verification.
Here are some industry examples where KYC is a mandatory requirement:
Cryptocurrency
Most cryptocurrency exchanges are required to follow the KYC framework because they fall under the category of Money Service Businesses (MSBs). Even though the original anonymous nature of crypto slowed down the development of regulatory measures, it didn’t stop to include this sector in the obliged entity list. Now, when addressing KYC requirements, cryptocurrency companies tend to use automated ID verification solutions that have global coverage, a user-friendly interface, and various KYC flow options tailored to different customer risk levels.
Ensuring effective KYC compliance helps deter money launderers and other financial criminals from becoming active on the crypto platform. To actually achieve this goal, The Financial Action Task Force (FATF) issued several red flags about users for crypto platforms:
- Creating multiple accounts under different names
- Providing incomplete KYC information
- Constantly changing their identification information
- Using forged or falsified identity documents or photographs
- Initiating transactions from non-trusted IP addresses
- Declining requests for ID verification or source of funds
- Sanctioned entities and customers who are on watchlists
Banking
KYC in the banking industry involves the procedures that banks follow to verify a client’s identity. These procedures involve tasks like verifying ID documents, screening for Politically Exposed Persons (PEPs) and individuals on sanctions lists, conducting face authentication checks, or biometric authentication. Thankfully, automated KYC software and technologies like optical character recognition (OCR) help improve AML programs for banks and ensure an efficient KYC process for the end user.
Establishing a robust KYC program is crucial because banks are frequently targeted by criminals for money laundering. To illustrate, individuals listed on sanctions lists often attempt to launder their money through illicit means, including spoofing, using fake IDs, and creating shell companies to conceal their true identities while funneling laundered money into the international financial system.
E-Commerce
KYC measures help e-commerce companies verify sellers and buyers. Identity verification in e-commerce consists of verifying account holders and their payment information. Sometimes, depending on the product or service, age verification can be enforced to confirm that the individual is of age.
Specifically, automated KYC solutions can create a smooth and secure customer onboarding process and enhance the overall services across various e-commerce platforms. As a result, identity verification has the potential to increase sales and improve customer experience for online retailers.
With identity verification, e-commerce companies can ensure secure transactions and lower the risks of fraud. In today’s digital scene, KYC is vital to guarantee such trust among users. Remember, they are the ones registering and purchasing on a digital platform, wanting to keep their data secure — free from credit card theft, confidential data misuse, and so on.
How Does KYC Differ Globally?
Several global organizations have created universal KYC and AML compliance recommendations. They are like guidelines for companies to implement the right measures and combat financial crimes. For example, FATF also has a set of 40 recommendations for its member states and offers model legislation that can serve as a foundation for new laws.
However, each country has the right to tailor the KYC framework to match its laws and regulations. That makes cross-border compliance a bit challenging for businesses, especially when it comes to large, global companies that are scaling fast and need to onboard customers from all over the world.
Here are some examples of KYC regulations based on different regions:
Europe
European Union member states possess the authority to develop their own KYC and AML laws. Consequently, the EU has issued a series of directives designed to provide guidance for these regulatory requirements. The latest directives, which are 5AMLD and 6AMLD, mandate that businesses must gather, verify, and maintain records of customers’ data and screen them against PEPs and adverse media lists to assess the overall risk.
Other EU regulations that obliged entities must follow include:
- The General Data Protection Regulation (GDPR) is the European Union’s response to the public’s demand for increased control over personal information.
- The Payments Services Directive (PSD2) is designed to foster customer-focused innovation in the banking sector, with a focus on preventing payment fraud and the misuse of digital financial tools.
- The revised Markets in Financial Instruments Directive (MiFID II) is driven by the need for greater transparency in financial investment activities.
Related: What are the EU’s Anti-Money Laundering Directives (AMLDs)?
United Kingdom
The Money Laundering Regulations of 2007, along with subsequent amendments, establish the KYC requirements in the United Kingdom. As a member of the FATF, the UK plays a pivotal role in shaping compliance regulations even outside the country. Notably, the FATF has recognized the UK as a “global leader” in compliance and transparency regarding KYC and fraud prevention.
Several key legislative acts in the UK include:
- The Proceeds of Crime Act 2002.
- The Money Laundering, Terrorist Financing, and Transfer of Funds Regulations.
- The Electronic Identification and Trust Services for Electronic Transactions Regulations (eIDAS).
In the UK, companies must also verify a customer’s name, address, and date of birth, preferably using a government-issued document that includes the customer’s photo, name, address, and date of birth.
Related: KYC Requirements in the UK
United States
KYC requirements in the United States originated from the 1970 Bank Secrecy Act (BSA). This act mandated that financial institutions must identify customers engaging in transactions and maintain appropriate transaction records.
At the very least, these laws mandate that financial institutions adopt a risk-based approach to verify a customer’s personal information and Social Security Number (SSN) or Employer Identification Number (EIN).
While the BSA also laid the foundation for AML laws in the US, it was crafted in an era prior to online banking. To adapt to technologies and emerging fraud risks, the US had approved new laws, including:
- Money Laundering and Financial Crimes Strategy Act (1998)
- USA PATRIOT Act (2001)
- Intelligence Reform & Terrorism Prevention Act (2004)
What is Corporate KYC (KYB)?
While ensuring the trustworthiness of individuals is important, organizations must also establish KYC processes for the businesses they intend to collaborate with and the people associated with those businesses. This process is called corporate KYC, known as Know Your Business (KYB).
Corporate KYC consists of the following steps:
- Conducting business verification. Organizations should gather and verify corporate details, including the business name, address, registration number, and other relevant business documents.
- Identifying Ultimate Beneficial Owners (UBOs). UBOs are individuals who exercise control over the company or hold a significant ownership stake.
- Implementing identity verification. Companies are required to conduct thorough ID verification checks on high-risk individuals, such as the mentioned UBOs.
Even though the regulatory framework mainly applies to financial institutions and related businesses, corporate KYC can be valuable for many companies, particularly B2B service providers. Through corporate KYC, you can have confidence in the legitimacy of your business partners. This process prevents unwanted losses, such as partnering with shell companies or related persons who are involved in money laundering schemes.
How Can You Streamline KYC?
Following all three KYC steps isn’t an easy task, especially for small businesses that don’t have internal compliance teams that would be able to build robust KYC strategies. Using automated software through a well-established third-party provider can minimize this hassle for you. At iDenfy, we can help you achieve this goal and turn manual, complex KYC practices into a smooth, streamlined process.
Our KYC solution (document, biometric, and manual) instantly extracts data from a large global ID document base. Additionally, you can add built-in AML screening checks and ensure ongoing compliance, as well as conduct address verification and other AML tools: adverse media checks, PEPs and sanctions screening, and more, including an automated Business Verification solution.
Get started here.