The discussion about fraud is ever-present in various industries worldwide – and for a good reason. Throughout the years, we, as a society, began to value transparency and fairness to a much greater extent than we did before. Fraud is directly opposing these values, and the demand for attention and prevention of fraud is rising every day.
The modern world is a favorable medium for fraudsters. For starters, most of our data currently resides in cyberspace and is susceptible to leaks and breaches. Furthermore, technological innovation is a double-sided coin. In an ideal world, it would only be used for moral purposes and to benefit society. However, we are far from such a world.
As technology becomes better, so do the methods criminals use to commit fraud. Forging documents, bypassing the safeguards, and faking biometric data are just a few examples of how technology allows fraudsters to become more devious than ever before.
iDenfy’s Experience with Fighting Fraud
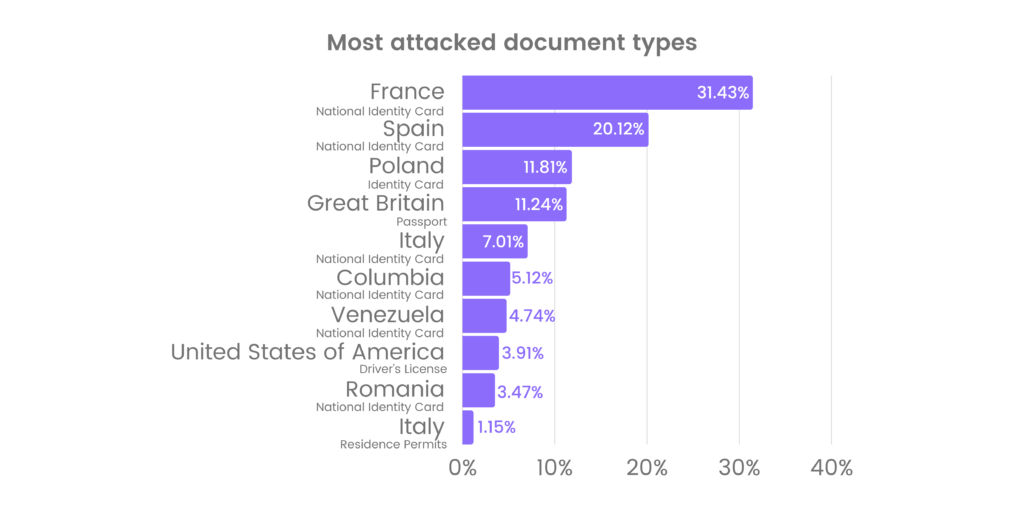
Since 2017, iDenfy has experienced a fair share of attempts to deceive its identity verification solution. There’s a pattern emerging – certain documents are forged to a much greater extent than others, and the reason for that is their susceptibility to falsification. 6/10 times, counterfeit documents involve national identity cards since they usually have little to no security measures. Furthermore, iDenfy’s team has noticed a disproportionate number of forgeries in some nationalities over others.
To present you with a better picture, here are the top five types of documents that we encounter most often when dealing with fraud:
- France’s National Identity Card – 31.43%
- Spain’s National Identity Card – 20.12%
- Poland’s Identity Card – 11.81%
- Great Britain’s Passport – 11.24%
- Italy’s National Identity Card – 7.01%
It’s important to note that most fraud cases can be prevented if companies take the necessary measures. And that’s where fraud week comes into place.
What is Fraud Week?
International fraud awareness week was started in 2000 by the Association of Certified Fraud Examiners (ACFE). It was a response to the rising number of frauds and has been held every November ever since. Hundreds of organizations worldwide come together to spread information about fraud in both their workplace and communities.
By becoming a part of this initiative, organizations can spread awareness about fraud very efficiently – ACFE has prepared a vast amount of material that can be shared inside the company and in its media campaigns to attract attention to fraud.
The benefits of participating in fraud week are immense. In addition to communities becoming more aware of fraud, the companies raising the awareness and providing anti-fraud training improve their bottom line value. According to a study by the ACFE, organizations that provided their employees with fraud training saw a 38 % decrease in fraud losses and a 33 % decrease in fraud duration.
Fraud week also results in participants getting creative in anti-fraud educations. Over the years, official supporters of the initiative have hosted company-wide trainings, competed in fraud-related games, publicly shared information in their communities, and much more.
Let’s take a closer look at what the fraud week entails in its program.
The Importance of Hotlines and Reporting Mechanisms for Preventing Fraud
Detecting fraud is only half the job when preventing it – an effective reporting mechanism, such as a hotline, is essential to the process. It allows organizations to send a tip more easily and encourages the process altogether – according to ACFE, companies with hotlines detected fraud by tip more often (49%) than those without (31%).
Additionally, hotlines also result in organizations noticing fraud much quicker and having more minor losses overall – hotlines in companies resulted in the median duration of fraud to be 12 months and median losses to stand at $100 000. In contrast, organizations without hotlines experienced a median fraud duration of 18 months and nearly doubled ($198 000) median losses.
How Internal Control Weaknesses Contribute to Fraud
Integrating internal control measures is an essential element of fraud prevention. Although there are many anti-fraud controls, ACFE has recognized four of them to be associated with at least a 50% reduction in both fraud losses and duration:
- A code of conduct,
- An internal audit department,
- Management’s certification of financial statements,
- Regular manager review of internal controls, processes, accounts, or transactions.
Even with anti-fraud controls set in place, fraudsters exploit the weaknesses in the system. Primary examples of these weaknesses are:
- Lack of internal controls,
- Lack of management review,
- Override of existing internal controls,
- Poor tone at the top.
Together these factors contribute to 78 % of occupational fraud. Thus, implementing internal controls and detecting weaknesses is a crucial part of managing fraud risk.
Common Computer and Internet Fraud Scheme
Fraudsters utilize the technology to their advantage in three main methods of computer and internet fraud:
- Phishing – the fraudster sends an email claiming to be from a legitimate organization and exploits the person’s naivety to gain sensitive personal information (name, address, social security number, etc.)
- SMSshing – a similar scheme, but the fraudster sends text messages rather than emails.
- Pharming – the fraudster creates a legitimately looking website designed to trick a person into inputting their sensitive data. They often gain access to a computer system via this fake website and install malware to collect the data about a person, monitor their login information, or lock them out of the computer system and demand payment to gain access to it again.
How is Money Laundered?
There are many money laundering schemes that people use to legitimize their illicit funds. ACFE presents us with the three common methods that fraudsters use:
- The middle man – the fraudster gives his money to a so-called middle man, who deposits it in various bank accounts in small sums. Whenever the money is needed again, the middle man withdraws and returns it.
- Gambling – the fraudster takes the illegitimate funds to a casino and exchanges them for chips. After several days they exchange it again for money, claiming good luck.
- Shell company – the fraudster sets up a shell company and deposits the illicit funds to the company’s bank account, falsifying the legitimacy of his income by claiming it as revenue.
What Does a Fraudster Look Like?
There are specific characteristics that are more common among fraudsters. According to ACFE:
- 69 % of them are men,
- 40 % are between the ages of 35 and 45,
- Most of them are in their company for more than a year,
- Almost half of them have university degrees,
- 53 % of them act alone in their schemes,
- 46 % of them live beyond their means,
- 88 % of them have never been charged before.
What Does Fraud Mean to You?
By definition, fraud is the intentional manipulation of the truth for financial or personal gain. Although you probably rarely think about fraud in your daily life, it’s an issue that affects you every day without you even noticing. Fraudsters target businesses, governments, and individuals. You should always ask questions and be alert. If something sounds too good to be true – it probably is. Be sure to report any suspicious activity to the relevant authorities to protect both yourself and your community.
What Is Identity Theft?
There are many ways fraudsters get a hold of personal information to commit identity theft – and most of them can be prevented:
- Make sure that any documents containing sensitive information are shredded before disposal,
- Wipe all hard drives when getting rid of electronics,
- Never send personal information via email or text messages,
- Confirm unknown callers claiming to represent a legitimate company,
- Avoid using unsecured public Wi-Fi networks,
- Check your billing statements and credit reports regularly to spot any suspicious activity.
Why Do People Commit Fraud?
Fraudsters often find themselves in a triangle of factors, leading them to commit fraud:
- Pressure from their personal issues, such as gambling, debt, or desires to live a high life,
- Opportunity to commit fraud, presented by a lack of internal controls and supervision inside the organization,
- Rationalization, such as the fraudster believing he deserves the money, blaming the circumstances, or convincing themselves they will pay the money back.
Final words
Fraud week raises awareness of the issues presented above. At iDenfy, we are glad to be a part of this initiative and encourage other organizations to join. Together we can make fraud obsolete! How? Contact us now! Click here to speak with a real person.




