Fraud Risks in Onboarding Systems
Most companies do not view onboarding as a high-risk area. It is usually seen as a routine step: collecting information, checking documents, opening accounts, and moving people through the process. Yet behind the scenes, onboarding is one of the busiest gateways in any organization, especially in user account, payments, or compliance-driven industries. And if a gateway gets busy, it can also become tempting to the wrong kind of traffic.
This is where understanding onboarding-related fraud risks becomes essential. Not because every applicant is looking unusual, but because every onboarding workflow needs defenses strong enough to avoid becoming a liability.
The Invisibility of Onboarding Decisions
Most organizations talk about onboarding in terms of efficiency: the fewer steps, the smoother the user journey. But behind every “faster process” sits an equally important question: What could go wrong if the wrong person gets through?
Onboarding is the earliest possible moment to verify identities, validate information, and confirm legitimacy. If something slips past this phase, it becomes much harder to catch later. Fraudulent accounts often blend into the system, moving unnoticed until money, trust, or data has already been lost.
Fraudsters know onboarding is the only moment when they can appear as someone else – using fabricated documents, fake identities, or genuine credentials that do not belong to them. Once they are past the gates, everything becomes exponentially more difficult.
This is why so much of fraud prevention depends on the strength and structure of onboarding systems, not just the controls later in the lifecycle.
How Fraud Reaches Onboarding
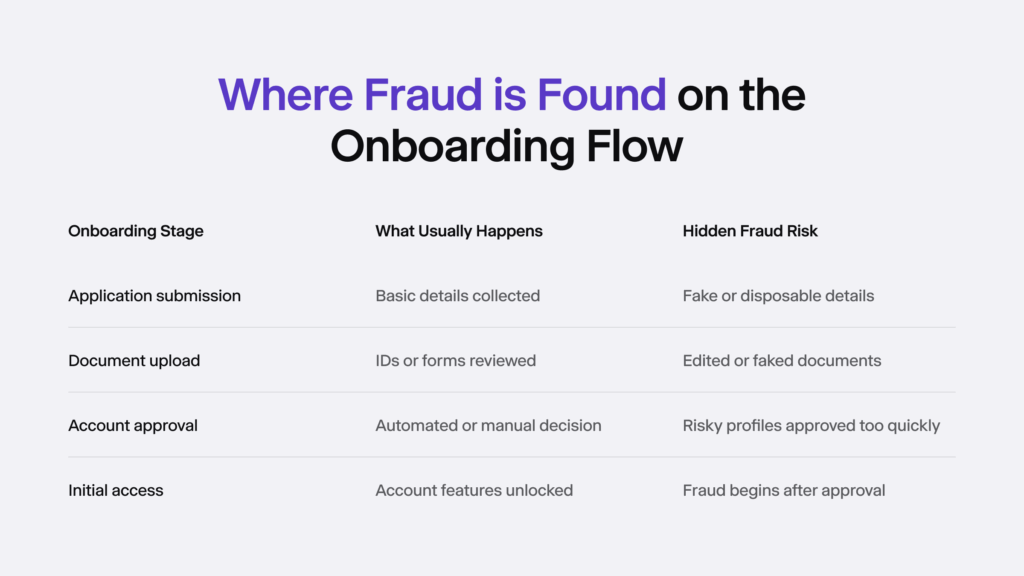
Every onboarding workflow has its own weak spots. Some exist because the system was designed years before fraud became so complicated. Others come from trying to keep things “fast and easy.” But across industries, the main risks usually fall under the same categories.
Below are the areas where fraud tends to slip in – often unnoticed until patterns emerge.
1. Identity Mismatches and Document Manipulation
For many onboarding systems, a document is still the starting point. But documents alone are easy targets. With high-resolution editing tools and cheap templates, forged documents no longer look like the obvious fakes people imagine. More importantly, onboarding teams often do not have time to examine every document manually.
Fraud in this stage ranges from slightly altered IDs to full fake identities. And while identity verification has improved tremendously, fraudsters have adapted just as quickly – especially in digital-only environments.
Companies often counter this with identity verification software, placing automated checks between the applicant and the approval process. These tools help match faces to IDs, detect tampering, and confirm legitimacy without slowing the process down. They will not eliminate every risk, but they close one of the biggest windows for manipulation.
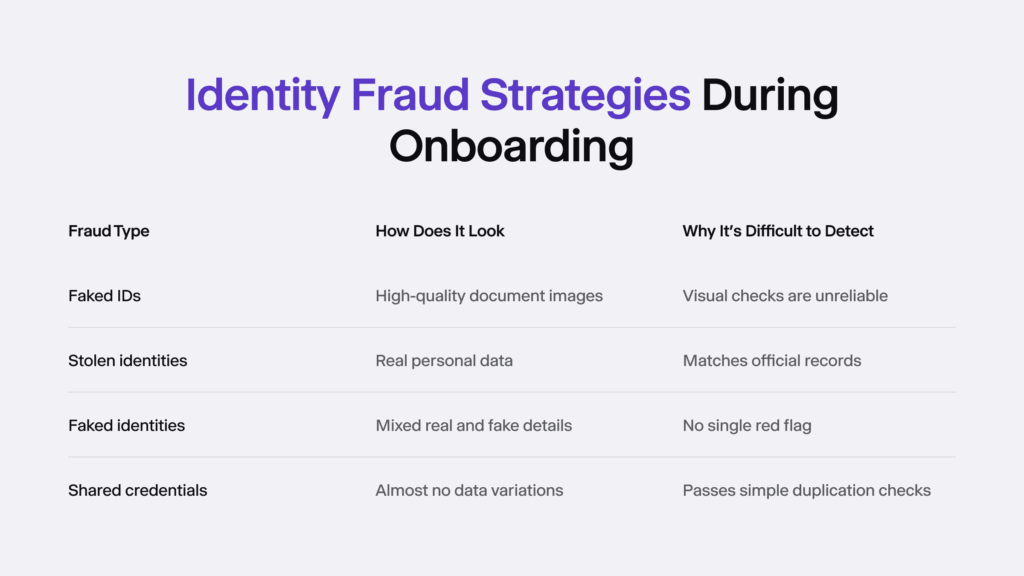
2. Fake Identities
Fake identity fraud feels almost low-effort, but it is one of the most expensive forms of fraud globally. Instead of stealing an identity, fraudsters build one from scratch – mixing real and fabricated information. The result is a user who does not actually exist but appears legitimate enough to pass surface-level checks.
The danger with fake identities is that they behave normally, at least for a while. They create accounts, build trust, and then disappear at the moment a financial opportunity appears.
These profiles are difficult to catch manually. They require pattern recognition, consistency checks, and layered data validation – all areas where automation plays a major role.
3. Multiple Accounts and Duplicate User Activity
People are not meant to have five or ten accounts within the same system, but onboarding processes that do not check for duplicates unintentionally allow it. Fraudsters rely on that oversight.
Multiple accounts can be used to:
- Access signup bonuses repeatedly
- Bypass restrictions
- Create fake “verified networks”
- Launder funds or move money undetected
Most organizations do not see this immediately because each account looks legitimate on its own. It is the pattern that reveals the truth – and patterns are easy to miss when approval steps are manual.
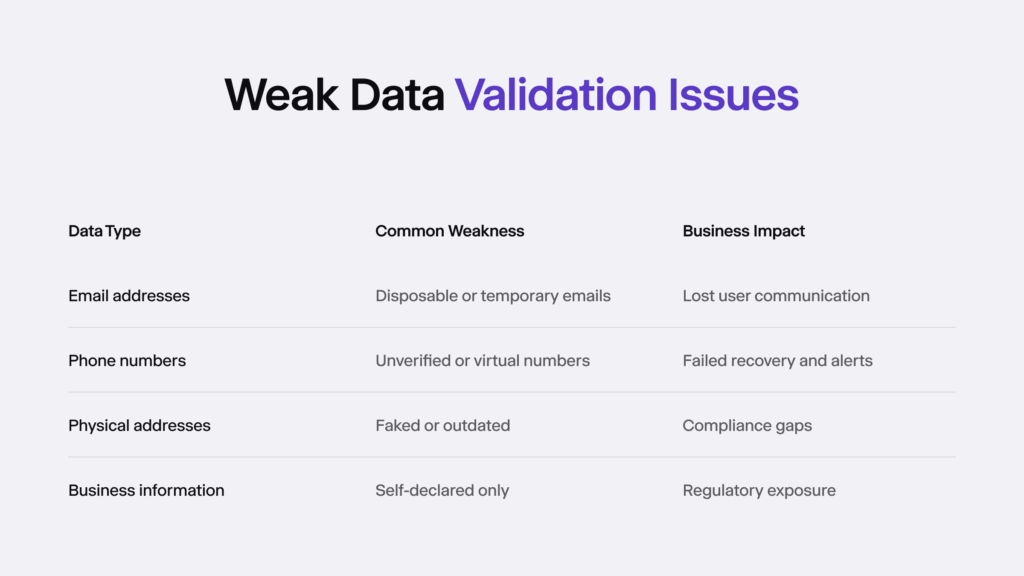
4. Weak Data Validation
Onboarding workflows often trust user-submitted data too easily: email addresses, phone numbers, company information, and even physical addresses, taking advantage by submitting disposable or fabricated data points – information that works long enough to get through the system but will not hold up later.
Weak validation creates bigger issues downstream:
- Bounced communications
- Abandoned accounts
- Chargebacks
- Compliance gaps
- Unresolved disputes
The solution is smarter validation – automating cross-checks, looking up databases, and analysing metadata, catching most inconsistencies before they become problems.
5. Insider and Process-Based Risks
Not all onboarding fraud comes from outside. Sometimes the vulnerability is the process itself. Misconfigured permissions, undocumented steps, or manual approvals create blind spots that malicious fraudsters can exploit.
This is about acknowledging that any system with too much manual involvement becomes fragile. When different people follow different steps, consistency disappears – and fraud thrives in inconsistency.
Related: [The Cost of Fraud]
Why Modern Fraud Looks So Different
Fraud today is not just smarter; it moves differently – fast, distributed, and coordinated through online communities where people share tips, tools, and templates – the barriers to entry are low. Someone who has never committed fraud can now buy everything needed to do so with a few clicks.
That is why onboarding is no longer about validation alone. It is about the context.
Fraud detection has shifted from “Does this document look real?” to:
- Does this person behave like a real user?
- Does this pattern resemble known fraud activity?
- Is this identity consistent across databases?
- Does anything about the submission feel artificially perfect?
Systems that treat onboarding as a simple administrative step fall behind quickly. The companies that stay ahead are the ones that design onboarding with a security mindset – quiet, invisible, and embedded within the workflow. In addition, due to modern fraud risks, many compliance teams has also turned to AI-powered OCR, in order to detect forged documents during onboarding journey and reduce manual review errors.
The Preventative Design
Companies that stay ahead of fraud do not just add more steps. They redesign onboarding so that fraud naturally becomes harder. Instead of relying on employees to spot unusual submissions, they create systems that recognize irregularities automatically.
This shift usually includes:
- Automated document checks
- Risk scoring during onboarding
- Identity matching and validation tools
- Behavioral monitoring
- Background database lookups
- Flexible workflows based on risk level
What is interesting is that this does not make onboarding slower. In most cases, it speeds it up because genuine users pass through more smoothly than before.
The Balance
One of the most difficult parts of building safer onboarding systems is avoiding friction for legitimate users. Long forms, multiple steps, or delayed approvals can make customers abandon the process altogether.
The goal is to create a quiet, structured system where risk is evaluated intelligently. Most people never notice the checks happening behind the scenes. They only notice when the process feels clunky.
Smart onboarding places heavier checks only where the risk is higher, and keeps the experience simple for everyone else.
Conclusion
Fraud does not attack the middle of the business, going straight to the beginning, where verification is weakest, and oversight is limited – that is why onboarding might feel administrative, but it is one of the most powerful places to block risk before it spreads.
Companies that invest in stronger onboarding – layered verification, smarter validation, and well-designed workflows create cleaner datasets, smoother user journeys, better compliance outcomes, and more resilient operations.