Where there are financial transactions and cash flow, there’s always a risk of fraud and money laundering. That’s why banks and all regulated entities need to follow strict processes that require verifying and screening users, as well as monitoring their financial behavior throughout the whole business relationship. The goal of fraud prevention is to spot inconsistencies that might lead to financial crimes. That’s why if a transaction is flagged as suspicious, investigators need to decide if it’s a false positive or if it needs to be reported to regulatory authorities.
But the issue is that internal compliance and Anti-Money Laundering (AML) teams often struggle with a large volume of transactions and other tasks that need to be done within a short period of time. Finding and flagging suspicious transactions might sound easy to some, but in reality, an AML investigation consists of multiple steps. More importantly, it needs to be optimized and built in a way that would fit the company’s capacity and would allow them to save costs without creating backlogs or disruptions to their clients.
So, what does it take to conduct an effective AML investigation and stay efficient while doing all the work, such as analyzing transaction patterns and checking links to high-risk entities? We explain it all and share best practices below.
What is an AML Investigation?
An AML investigation is the process of identifying suspicious activity through investigations that ultimately consist of multiple processes, like analyzing transactions and customer behavior to detect terrorism financing, money laundering, and other financial crimes. The findings need to be inspected during the AML investigation as a way to identify if the funds are legitimate and not disguised to hide money laundering.
This helps internal teams to determine if the activity:
- Is legitimate
- Needs to be reported by filing a Suspicious Activity Report (SAR)
Investigators often use an automated AML system that is able to flag an atypical transaction or customer activity, which follows a trigger and the need to review the detected red flag in a more detailed way, for example, by checking the customer’s personal details, previous transaction patterns and overall financial behavior. For example, compliance teams look for other suspicious signs that might indicate fraud, such as connections to sanctioned entities or high-risk individuals.
Why is it Important to Conduct an AML Investigation?
The reason is simple. AML investigations help detect and prevent all sorts of unwanted illicit activity, which can be infiltrated. For example, criminal gangs can use a money mule, a person who has a clean record and doesn’t ring any bells of danger. However, such people are used to laundering money without a trace, often gaining a commission or even being used a a channel without their consent.
Essentially, an AML investigation helps:
- Protect the financial system and identify crime, such as corruption or money laundering.
- Maintain financial integrity and ensure compliance once suspicious activity is reported to regulatory authorities.
- Prevent financial abuse and stop financial institutions from being used for crime, such as fraud and the reputational damage that comes with it.
So, in this sense, AML investigations are part of a bigger AML program that requires extensive work to ensure AML compliance and guarantee a transparent financial system. That’s why, without any sort of automation, many internal AML departments struggle and have more work than actual resources.
What Indicators Can Trigger AML Investigations?
There are certain AML red flags or triggers that investigators need to be aware of when initiating an AML investigation.
Most common ones include:
🔴 Unusual Transaction Patterns
This includes abnormally large amounts of transactions, unexpected changes in a customer’s financial behavior and other similar events that are linked to unusual transactions.
Other indicators that can trigger AML investigations related to unusual transaction patterns include:
- Smurfing, which is the process of dividing large sums into smaller transactions on purpose to avoid hitting AML alerts and reporting thresholds.
- Sudden changes, which often impact transaction frequency or size, show signs of change in terms of the typical financial profile.
- High-value transactions, such as a large transfer, are especially targeted at customers who typically make small deposits and transfers.
Simply put, when a certain action no longer aligns with a customer’s expected behavior, it signals a potential AML risk, which requires analysts to dig deeper and review the case manually.
🔴 Connections to High-Risk Individuals or Entities
Customers linked to entities with complex corporate structures or individuals in public roles, known as Politically Exposed Persons (PEPs), are naturally considered to be high-risk due to their potential for a bigger chance of involvement in financial crime, for example, corruption and bribery. PEPs have access to public funds and hold power in terms of decision-making. In the meantime, high-risk entities can be shell companies that only exist on paper and are used to launder funds, as well as sanctioned entities.
That’s why it’s important to assess risks and review any links or relationships with such clients as a way to determine if the risk is real. This helps carefully prevent misuse of the financial system.
🔴 Sudden Financial Changes
Frequent transfers that are abnormal or constant and unexplained movement of funds between accounts can also trigger an AML investigation due to the increased risk of money laundering. Investigators look for a clear purpose of the transaction; whether it’s for personal or business use, it needs to be valid.
Suspicious changes that need to be investigated in a more detailed way often include cases like:
- Rapid movement of funds, often using cross-border transactions and international accounts in different countries, without a clear reason why, for example, a business in country A might want to use an account in country B with no relation to its business operations.
- Short-lived accounts, which are opened and closed quickly, show a sudden, suspicious burst of activity without any legitimate operations. This can be treated as a possible indication that such accounts are being used for money laundering.
Usually, when people change jobs or relocate, they can showcase a pattern of at least a minor financial shift. However, if the change is excessive and lacks a reason and explanation, or proof of income, it’s seen as a valid reason to trigger an AML investigation.
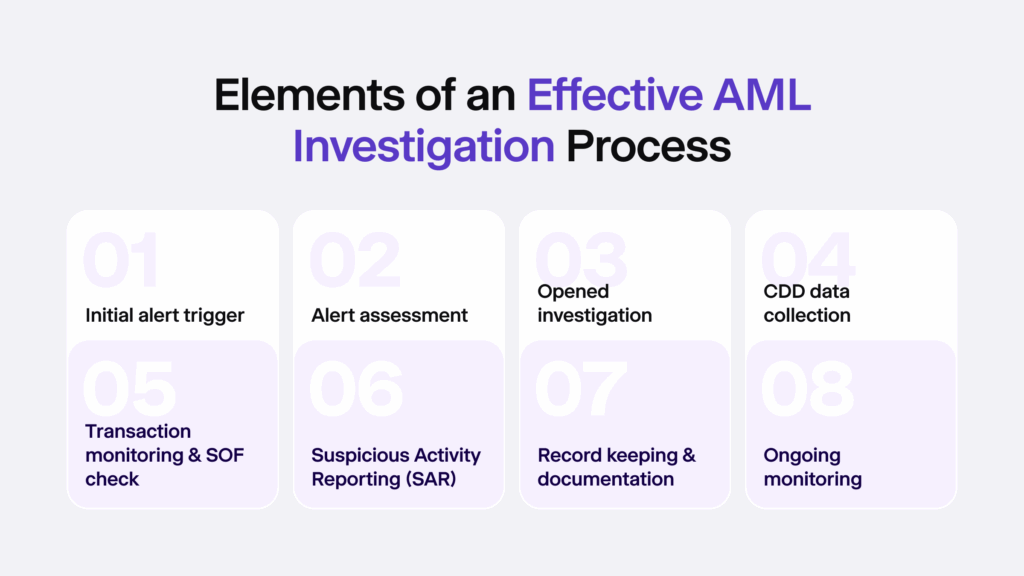
What Steps Complete the AML Investigation Process?
Here’s what goes into an AML investigation process:
🟢 Alert Trigger
A trigger event marks the start of when analysts need to move forward with the AML investigation. This “flag” is often found using an AML system that identifies suspicious patterns, flagging the activity for further review.
Alerts are often generated when:
- Unusual patterns, such as large transfers or high-risk user behavior, are detected.
- Customer due diligence (CDD) checks show a potential AML red flag, including other cases when a trigger is found via third-party reports or requests from law enforcement.
The goal is to find out the real reason behind the AML trigger based on collected documents and other pieces of evidence without being biased. This ensures fair and transparent conclusions along with well-planned further steps of the AML investigation.
🟢 Alert Assessment and Decision Making
This is the phase of the investigation where you need to determine whether the trigger is dangerous and actually worth a full review.
Investigators need to assess and validate the alert by:
- Reviewing the customer’s profile, including their account activity during the review period, to see if it aligns with their risk profile based on different risk factors, such as their business or occupation.
- Prioritizing high-risk alerts, which means filtering out signals that do not translate into a real risk. The most suspicious triggers need to be investigated first.
This is common, since false positives are an issue for many, even when using advanced software, and allocating the team’s resources efficiently is very important.
🟢 Opened Investigation and Due Diligence
Doing due diligence and ensuring that you have all the necessary information about the customer is one of the most important parts of the whole AML investigation process.
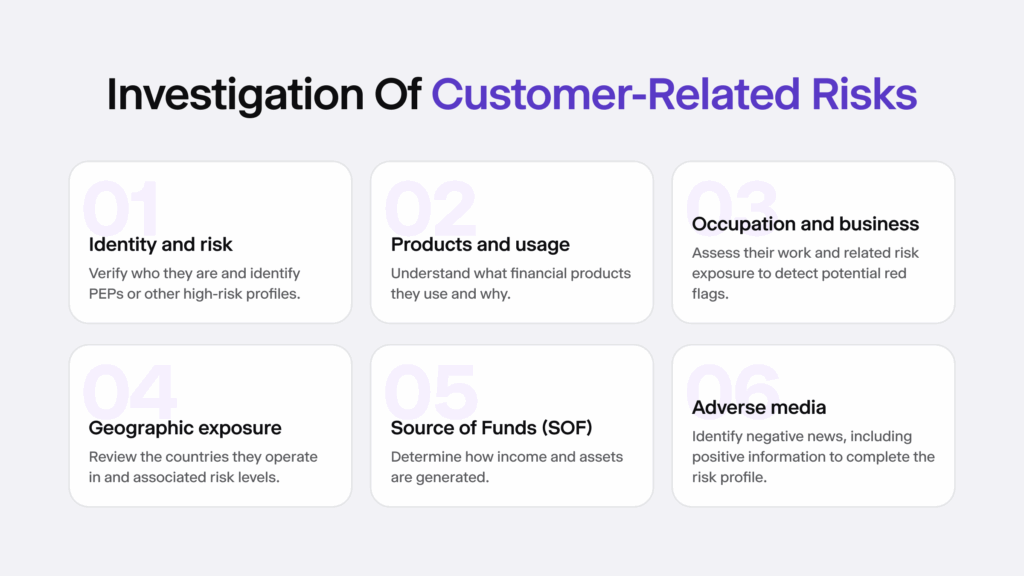
Collecting information about the customer means conducting Know Your Customer (KYC) verification and answering questions, such as:
- Who they are and what kind of risk they carry (perhaps they have a PEP status)
- What they do for work, including details about their business or their profession and then the risks behind the industry or concrete work that they do
- How they earned their income and what kind of assets they have that made an impact and allowed them to build their wealth
- Where they are based, and if they are linked to any high-risk regions with high money laundering and corruption rates.
- If there is adverse media and any news about them online, especially information about their business and family.
Depending on the alert, CDD and Enhanced Due Diligence (EDD) measures are applied, and the data is collected from various databases, such as government records, as well as branch-level files, and internal company records.
🟢 Further Risk Assessment
After the investigators confirm that the alert is credible, the next step is to collect and analyze information to assess the risks linked to that particular trigger. Typically, the main focus goes into suspicious signs and not the typical financial behavior, like transactions for rent or mortgage, which are typical of the monthly history log.
To understand the context and purpose of financial activity, investigators:
- Review transaction histories, customer profiles, and other linked information that is relevant to that particular case.
- Examine suspicious patterns against typical AML risks and universal behaviors to determine whether the activity is actually suspicious or potentially illegal.
For example, for business accounts, regular payments, such as taxes, utility bills, legal fees, payroll, and supplier invoices, should match the scale of the business.
➡️ Pro tip: Focus and allocate your resources not on transactions or user behavior that is normal, but only on what seems out of character for them to save time.
🟢 Evidence Collection and Reporting
Collecting evidence means looking for hidden crimes and determining whether a predicate offense, such as fraud, as in the original crime that generated the illicit funds, can be identified. In this stage, investigators look for any links to money laundering, tax evasion, and other crimes to confirm that the flagged incident is legitimate.
Next, there are two outcomes:
- If investigators don’t find genuine offenses regarding the customer, they further assess the situation to determine the reason and legal grounds for the suspicion, for example, by identifying money laundering indicators.
- If investigators confirm the case as legitimate and a predicate offense is established, for example, such as concealed illicit movement of funds, it should be reported to the legal authorities through a Suspicious Activity Report (SAR).

If the suspicious activity is deemed as legitimate, the company can terminate the user’s account, depending on the operating industry, local/global regulations, and the scale of the offence.
What are the Main Challenges of AML Investigations?
Customers who try to avoid providing certain documents or extra information, inaccurate data with gaps in customer profiles and financial information, etc. The list goes on. AML analysts and many compliance teams, especially those that deal with a large volume of transactions, sometimes struggle when conducting investigations.
Apart from the gaps in user information, popular reasons for these issues include:
- The lack of skilled AML investigators. Even with AI chatbots and suggestions from a proper AML software like iDenfy’s AML platform, AML investigations require highly skilled and trained professionals who can handle complex, traditionally lengthy cases efficiently.
- The constant flood of AML alerts. Often, a large portion of the flags found by the software can be filled with false positives, which shifts the focus from critical AML red flags that need to be manually assessed and reported.
Not implementing ongoing monitoring measures or keeping poor enhanced due diligence and risk management practices can result in non-compliance. For banks and other regulated entities, this means huge fines and reputational damage, which automatically translates to loss of trust or even losing customers to competitors. More importantly, poor AML investigations can become the main reason why a financial institution becomes a channel for money laundering.
Final Thoughts
Sanctions change, cyber threats evolve, AI fraud id getting more intense and major regulations are imposed on more and more sectors, which are all factors that lead to more companies upgrading their AML systems and using more advanced, AI-powered platforms that have AML case management capabilities, built-in PEPs and sanctions screening, and ongoing monitoring options for easier, audit-ready logging and suspicious activity reporting.
Other external factors that impact AML rules and the whole investigation process include ongoing geopolitical tensions. In practice, not having the right or updated sanctions lists and PEP data or AI-powered risk assessment software makes it practically impossible to stay compliant without breaching AML laws or spending hours on a single investigation.
At iDenfy, we make sure you don’t miss any critical red flags, ensure global AML compliance, minimize false positives, and build your own tailored AML workflow, depending on your industry.
Take a look at our AML Screening and Monitoring solution, or book a free demo to see it in action right away.