In the modern age, adapting to the rapid pace of technology is becoming increasingly challenging. Traditional channels are being replaced by digital alternatives, and numerous companies and institutions are struggling to keep up with the growing demands of cybersecurity. Synthetic identity fraud serves as a prime example of this issue.
However, what exactly is synthetic identity theft, and how big of an issue is it? Let’s get right into it.
The Definition and Explanation of Synthetic Identity Fraud
Synthetic identity fraud is the use of a combination of personally identifiable information to fabricate a person or entity in order to commit a dishonest act for personal or financial gain.
Fraudsters create a new identity by combining fabricated and genuine information, such as Social Security Numbers (SSNs) and names. This synthetic identity is then utilized by criminals to deceive financial institutions, government agencies, or individuals. Criminals can later use this tactic to open new accounts and make fraudulent purchases, which automatically results in financial harm to their victims.
There are two main categories of synthetic identity fraud:
- Manufactured synthetic identity fraud. It involves combining real and fake information to create a completely new identity.
- Manipulated synthetic identity fraud. It occurs when a genuine identity is used, but certain personal details are specifically modified. This type of fraud is relatively easier to identify and detect.
Verify customers identity within 15 seconds. Schedule a free identity verification demo here.
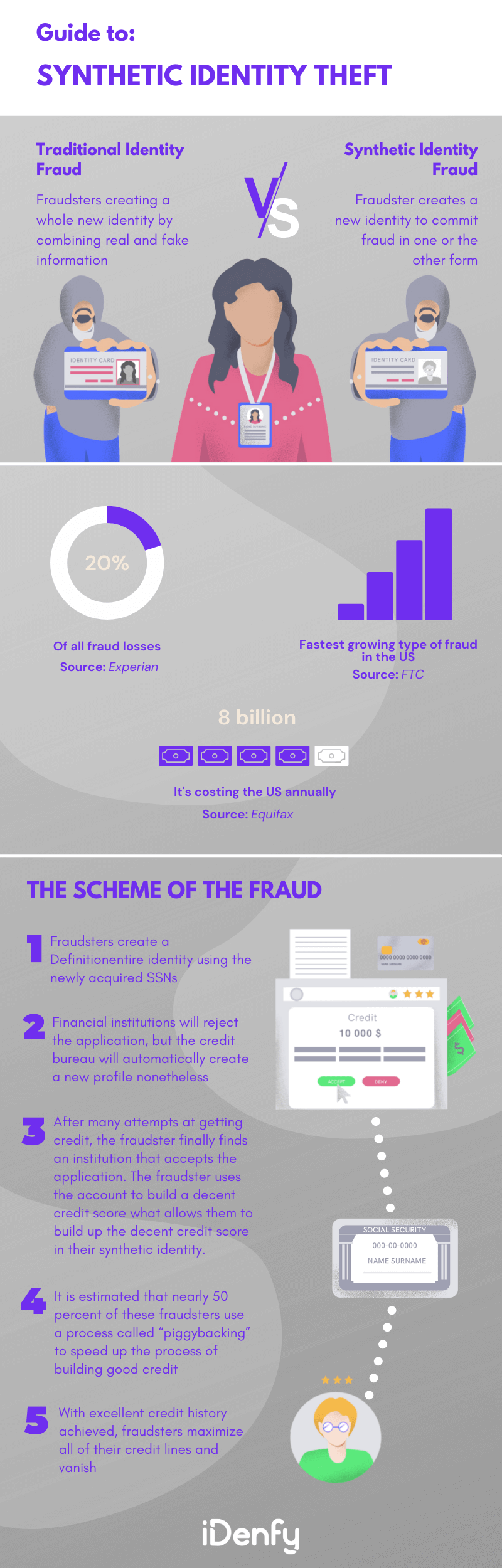
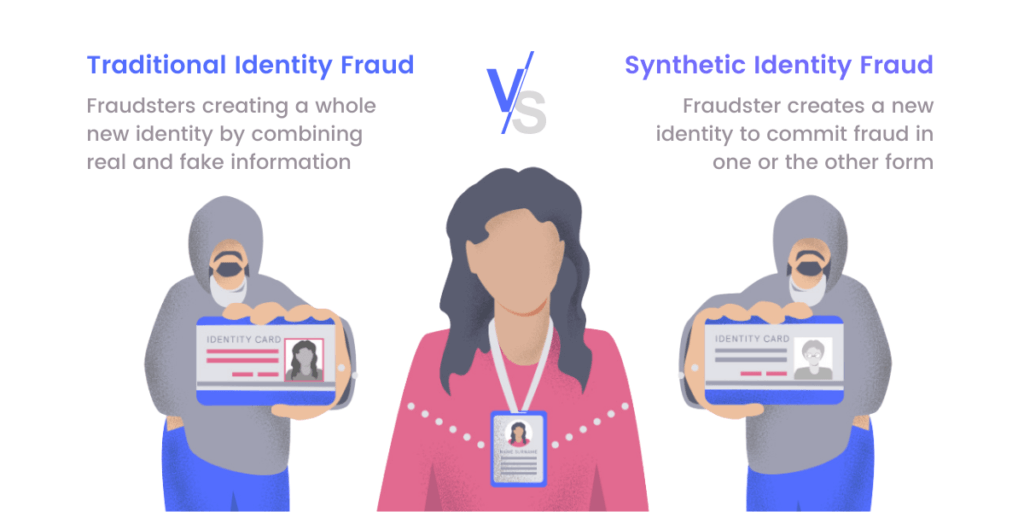
Synthetic Identity Theft vs Traditional Identity Theft
Synthetic identity theft occurs when an individual combines genuine and counterfeit identity details. This real information is often obtained through theft, while counterfeit details like a false name, date of birth, or address are added. Thanks to the nature of combining different identity information, this synthetic identity theft is sometimes referred to as a “Frankenstein identity.”
Traditional identity theft involves stealing someone’s identity as a whole. It’s usually achieved by purchasing the victim’s personal information (name, social security number, date of birth, etc.) via the black market and is most frequently used to open credit card accounts.
The main difference between synthetic identity theft and traditional identity theft lies in the approach used by the criminals. Traditional identity theft involves stealing and using someone’s genuine personal information, while synthetic identity theft involves creating a new identity by combining real and fake information, making it harder to detect and trace.
The Impact of Synthetic Identity Theft

Synthetic identity theft is most rampant in the United States. A person’s SSN generally remains the same throughout their lifetime. It creates a medium for it to be used universally as an identifier by both private industry and various government agencies. Children are particularly vulnerable targets of synthetic identity fraud because it may take several years to realize their SSN has been compromised.
Useful and convenient as it may be, SSNs have become a prime tool for committing fraud. On the dark web, where fraudsters generally find personally identifiable information for a purchase, SSNs are sold for as cheap as 1$. Generally, those are the SSNs of children, homeless people, or elderly – people who are least likely to check their credit information regularly.
Not only individuals but also businesses are suffering significant financial losses due to synthetic identity fraud, which results in the loss of billions of dollars. Not to mention the fact that organizations need to invest countless hours in monitoring individuals who might be entirely fictional. So in light of an alarming number of data breaches and personal detail availability on the dark web, it’s no longer sufficient to rely solely traditional tools which are incapable of detecting synthetic identity fraud.
Ensure your customers are real. Schedule a free demo here.
How Does Identity Fraud Happen? A Step-by-Step Scheme

After acquiring the data, fraudsters generally follow a step-by-step scheme:
Step #1: Fraudsters create an entire identity using the newly acquired SSNs, consisting of both real and fictional data. Even though it is then used for various fraudulent activities, the most common among them is applying for credit cards.
Step #2: Most financial institutions will reject the application, but the credit bureau will automatically create a new profile nonetheless, which then becomes proof of existence for the false identity.
Step #3: After many attempts at getting credit, the fraudster finally finds an institution that accepts the application. More often than not, it is a high-risk lender. The fraudster uses the account to build a decent credit score by making timely payments, making them a trustworthy person in the eyes of various lenders, now including those of low-risk. It also allows the fraudster to access higher credit limits, which furthers his needs. This process can go on for years before it’s detected, allowing them to build up the trust of institutions in their synthetic identity.
Step #4: It’s estimated that nearly 50% of these fraudsters use a process called piggybacking to speed up the process of building good credit. It’s a process of becoming an authorized user of an account with good credit history and results in compensation for this account’s holder.
To achieve this, fraudsters employ a variety of tactics, which include:
- Falsifying identification documents
- Establishing social media presence on fake accounts
- Creating fake businesses
- Using drop addresses to receive/forward credit cards to alternate locations
Step #5: When excellent credit history is achieved, fraudsters maximize all of their credit lines and vanish. Ironically, some even double the payout, claiming identity theft, which results in all of the charges being removed. Other times, criminals use fake checks to restore the balances in their accounts and max out on credit once more before finally disappearing for good. However, only the fake identity is gone, and the fraudster synthesizes a new one to repeat the process all over again. That’s how they leave institutions to chase ghosts.
Synthetic Identity Fraud in Numbers
According to the Aite Group, synthetic identity theft has resulted in an estimated $2.43 billion in fraud losses in 2023. The Federal Reserve reports that synthetic identity fraud cost lenders $6 billion in 2016 alone. Fraudsters target children’s SSNs disproportionally, and it might result in them having to jump through hoops in order to prove in the future that fraudsters have compromised their credit history.
The era of digital age sets the stage for synthetic identity fraud to become the fastest-growing type of financial crime in the United States. Although it’s not as prevalent in Europe, more than half of fraudsters apply for credits online, and the gaps in identity verification systems worldwide are exploited immensely by synthetic identities.
Fraud detection and prevention service from market leaders. Schedule a free demo here.
Solutions to Prevent Synthetic Identity Fraud
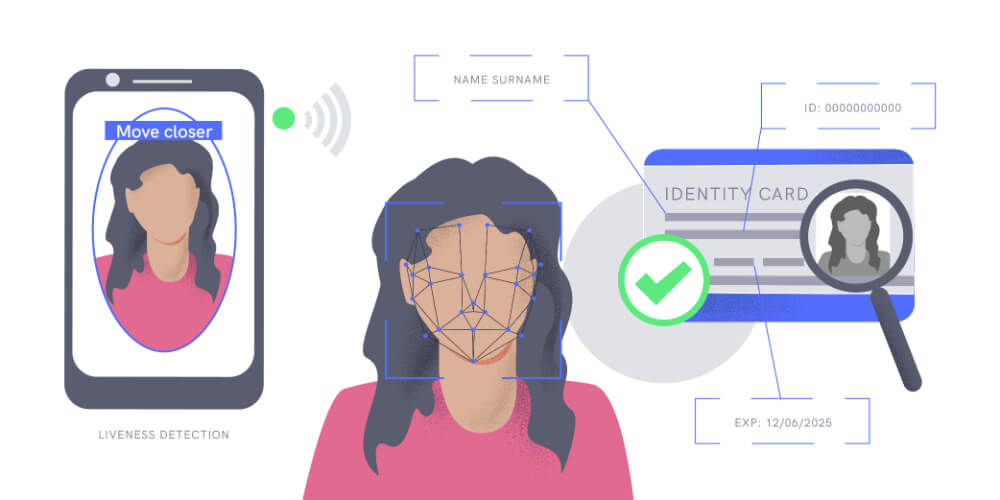
Due to the dangers behind synthetic identity fraud, organizations should implement more sophisticated strategies for identity verification – both to minimize their losses to fraudulent activity and to build trust among their clients.
iDenfy can become a great solution to this problem. It employs a 4-step verification process and combines Liveness Detection, ID Verification, and Facial Recognition. The automatic ID document detection verifies whether the documents are not forged or tampered with in any way and if it meets security requirements.
Combined with real-time human supervision, our AI algorithms detect fraudulent identity documents and ensure a much safer process, stopping fraudulent activity in its tracks. We’re currently supporting 3000+ identity documents across 190+ countries.
Keen on learning more? Get a free demo, or get started right away.
This blog post was updated on the 11th of July, 2023, to reflect the latest insights.