The purpose of the reverification process is to check and confirm the identity of a customer who has previously completed the verification process. A lot of businesses use reverification when customers are involved in a high-risk action after their initial onboarding stage. For example, it can be useful to initiate reverification after the customer changes their personal information, such as their address info or their documents expiring.
While many businesses perceive identity verification as a one-time requirement, the reality is that the initial verification is typically just the starting point. That’s why reverification helps businesses maintain up-to-date information about their customers and can detect alterations in their risk profile.
Some industries mandate reverification, and it serves as a protective measure for both the company and its customers. This ensures compliance with regulatory standards and aids in the proactive management of potential risks associated with customers.
However, reverification can be beneficial for non-regulated entities as an extra security measure against account takeovers and other types of fraud. Let’s find out how exactly that is possible.
What is Reverification?
Reverification is a process designed to reassess a customer’s information by verifying their identity again after the initial identity verification process. This systematic practice checks the correctness of a customer’s information and risk profile, which is a vital part of ongoing customer due diligence (CDD) and the risk-based approach (RBA) to anti-money laundering (AML) compliance.
For example, landlords in the prop-tech industry use reverification, as it allows them to confirm the identity of potential tenants before entering into a business relationship with them. In particular, reverification processes depend on biometric technology. Compared to traditional verification, reverification is an efficient, simple, and user-friendly process that swiftly confirms the user’s identity. If the reverification fails, the company can proceed with the next appropriate steps, ensuring they don’t become entangled with a fraudulent customer.
Use Cases for Reverification
When it is required to use the reverification process depends on the business, industry specifics, and user expectations, as well as mandatory regulatory requirements. However, re-verifying customers plays a vital role in every digital company’s growth and development for maintaining user trust.
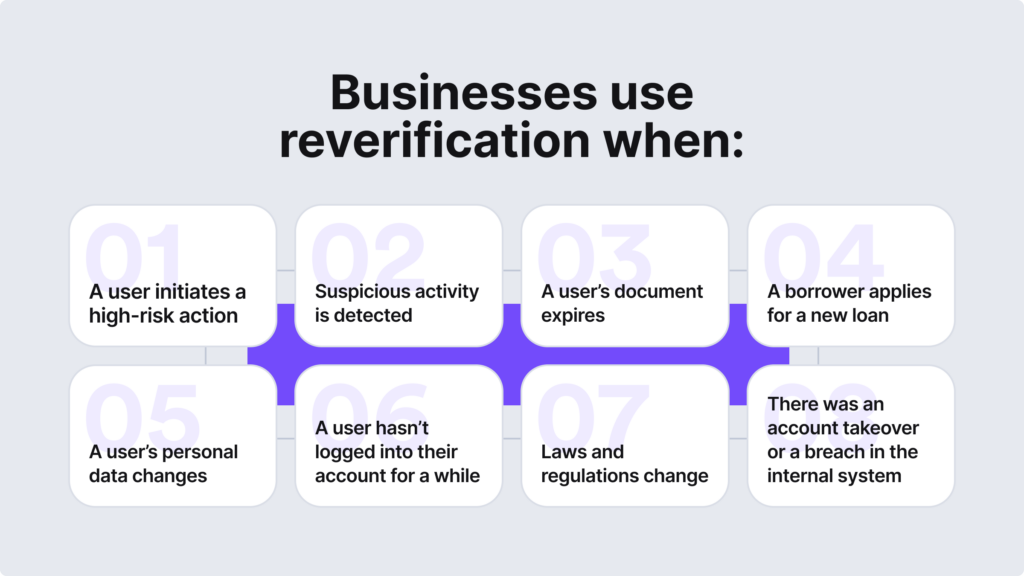
Companies often use the reverification process in various use case scenarios, including when:
- A customer’s document expires.
- There’s a change in the customer’s personal data.
- There’s a higher risk of money laundering and other financial crimes.
- Suspicious activity, such as a fraudulent IP address, is detected.
- A customer’s data was compromised, for example, due to an account takeover.
- A customer hasn’t logged into their account for a long period of time.
If the business must comply with AML or Know Your Customer (KYC) regulations that require integrating identity verification, they may be required to reverify existing users in the event of changes to regulatory compliance requirements. On top of that, the reverification process enables regulated entities to update high-risk customers subjected to Enhanced Due Diligence (EDD). This helps conduct an accurate assessment of potential risks associated with the customer’s activities.
Why is Reverification Important?
If your business is under KYC regulations, reverification is important because it’s a mandatory requirement. For example, ongoing monitoring is a vital element of KYC programs, working alongside CDD and ID verification. While this third step of the KYC is associated with continuous transaction and customer behavior tracking, it also consists of periodic reverification, as well as conducting AML screening. For example, sanctions lists, adverse media, watchlists, and politically exposed persons (PEPs) lists.
Reverification is crucial to adjust to changes in a customer’s identity, such as contact details or financial information. In general, the key reason why reverification is important is that the process enables companies to understand their customers’ risk profiles better. This helps them implement effective risk management strategies. Additionally, by reverifying customer data, companies can improve their ability to identify and prevent money laundering, terrorist financing, and other illicit activities.
Related: Face Authentication — Why It Completes Your Identity Verification
Benefits of Reverification for Businesses
Reverification is beneficial for businesses because it ensures the accuracy of customer information over time. That said, there are other key benefits to this process:
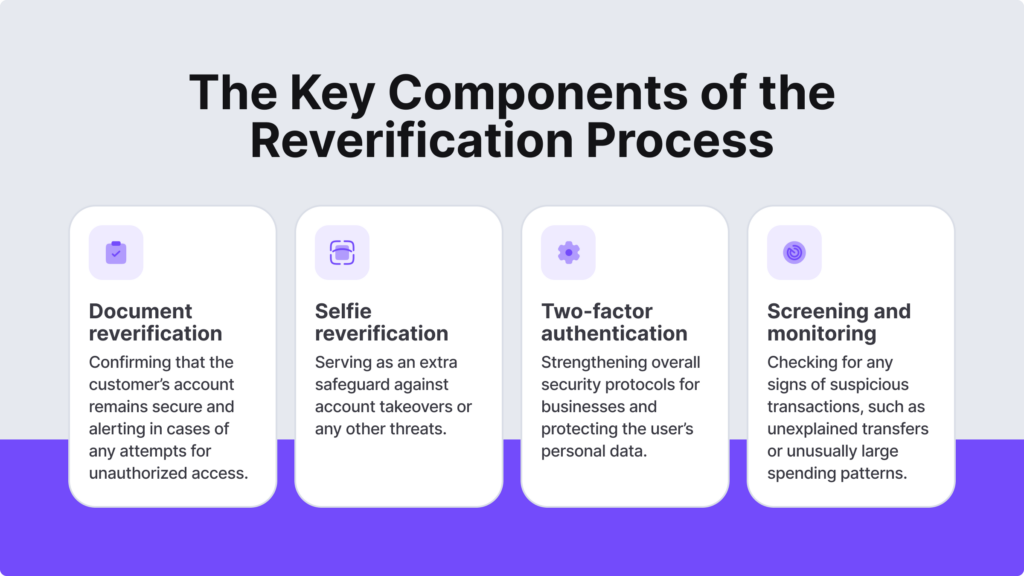
- Protection against account takeovers. Reverification serves as a safeguard against account takeovers, confirming that a customer’s account remains secure and alerting in cases of any attempts for unauthorized access. For example, If a customer has been inactive for an extended period, asking them to reverify their identity adds an extra layer of protection.
- Improved monitoring of customer accounts. Reverification helps companies conduct enhanced customer activity monitoring. That includes checking for any signs of suspicious transactions, such as unexplained transfers or unusually large spending patterns that sometimes can signal identity theft.
- Better risk management. Reverification is based on a proactive approach that strengthens overall security protocols for businesses, mitigating financial crimes and other threats in a timely manner. For example, when an existing borrower seeks a new loan, essential details like income and credit report can be reverified to confirm their eligibility and prevent illicit activities.
What Checks are Included in the Reverification Process?
The reverification process consists of three standard types: document reverification, reverification of another individual or business, and reverification of assets. For example, if the business is obliged to verify a person’s net worth, they conduct reverification by analyzing the person’s assets, such as stocks or real estate.
In practice, the reverification process can be layered into several different checks, for example:
Government ID Document Reverification
In the process of reverification, companies have the goal of confirming the accuracy of the customer’s identity data. This includes validating official government-issued ID documents (passports, driver’s licenses, US military cards, permanent resident cards, etc.) to re-verify that the customer’s identity data aligns with the latest information on record.
Reverification of government IDs can be necessary under various circumstances, such as when the company identifies an expired ID, when a customer seeks to regain access to their blocked account following a potential ATO attack, or in case of sudden and significant changes to their personal information.
Selfie Reverification
Some companies that incorporate selfie verification may request users to submit multiple pictures, such as a standard profile selfie or one with the user looking to the right. This additional step is implemented to confirm the user’s real-time presence during the reverification process using selfies. The obtained selfies are compared with either a photo ID, like a driver’s license, or a previously submitted selfie.
The purpose behind this practice is to safeguard against fraudulent attempts, including the use of deepfakes, masks, manipulated photos, and other deceptive methods aimed at circumventing the reverification process. In addition, some industries, for example, online marketplaces selling age-restricted products or services, use selfie reverification to confirm a customer’s legal age with each order.
Two-Factor Authentication (2FA)
Two-factor authentication (2FA) is another type of check used for the reverification process. Businesses can incorporate 2FA into their reverification process by prompting the users to enter their standard credentials, for example, username and password, and asking them to provide a second form of identification. In this 2FA reverification stage, users receive a temporary code sent to their mobile device.
It’s worth noting that while 2FA can increase the difficulty for malicious actors to compromise accounts, it does not verify the identity of the person signing up. Without a biometric scan, this reverification model typically operates on the principle that only the authorized user has access to the device, which may not always be accurate. However, it doesn’t add unnecessary friction, and for the end-customer, provides a passwordless alternative to reverify their account.
Continuous Rescreening and Monitoring
With all the types of reverification checks, continuous customer rescreening and ongoing monitoring are crucial to maintaining a vigilant stance on risk levels, involving the ongoing scrutiny of both customers and their transactions. When a business initially brings a new customer, a crucial aspect of the KYC/AML compliance program typically includes screening the individual against various lists and reports.

Regularly updating and reverifying customer information is essential to ensuring that risk assessments stay accurate and timely, reflecting the current state of the business. This step in reverification is crucial because PEPs and sanctions lists, for example, change over time. For this reason, rescreening of users helps ensure accurate risk profiles and ongoing compliance.
How to Maintain a Smooth Customer Reverification Process?
From a user’s perspective, customer reverification is a necessary process, yet also an inconvenience. While users want to protect their data, the extra authentication steps can be seen as another mandatory process that adds an unnecessary layer of hassle, especially if not done right. To maintain a smooth reverification process, businesses need to prove to their customers that they can build a quick and efficient method to confirm whether an account has been compromised, taking seconds.
Similarly, like with traditional identity verification, the process of reverification aims to maximize the identification of genuine users with legitimate intentions while minimizing the risk of fraudulent activity. KYC compliance regulations are influenced by many factors, including the customer’s jurisdiction, internal company system, and more.
However, there’s a list of potential combinations of checks custom reverification procedures can be tailored to these specifics, helping companies maintain a smooth reverification process that contributes to a more personalized user experience. When customers encounter a seamless reverification process during challenging situations, such as a potential account takeover, for example, they tend to keep using the company’s services.
This is extremely important for businesses that are trying to keep up with the fast-paced environment and the growing customer expectations. At iDenfy, we can help you automate customer onboarding for increased speed and, at the same time, increase convenience with a swift face re-authentication check.
Talk to us to find out more.