Transaction screening and monitoring play vital roles in detecting and preventing money laundering, counter-terrorism financing (AML/CFT), and other types of fraud. Both processes are vital for businesses, as to this day, money laundering presents a major challenge globally, with annual figures ranging from $800 billion to $2 trillion. The inability to identify and stop the laundering of such large amounts of money carries consequences, including fines for financial institutions and lost tax revenue for governments.
Consequently, governments have a strong motivation to combat money laundering, leading to a unified approach of strict AML regulations worldwide. For example, the Financial Action Task Force (FATF) has issued a set of 40 recommendations urging governments to adopt measures like screening and monitoring to mitigate the risks associated with money laundering and other crimes.
To put it simply, while both transaction screening and transaction monitoring are separate concepts, they share similarities. Screening involves assessing risks before the transactions. In the meantime, monitoring is linked to assessing transactions and accounts after they have taken place.
In this blog post, we take a closer look into both processes, finding out the key details and why they’re important for AML compliance.
What is Transaction Screening?
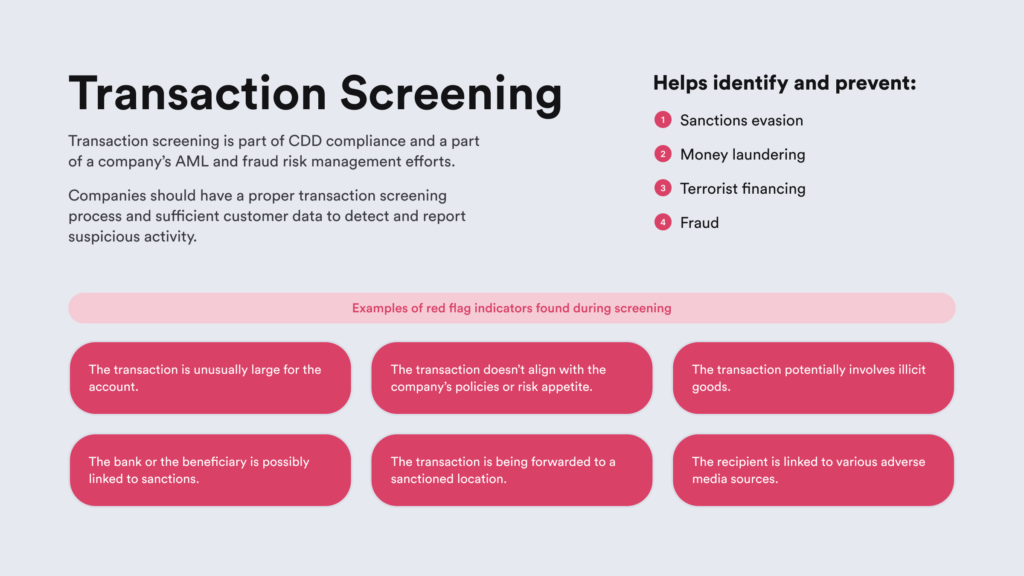
Transaction screening is a process designed to examine transactions in order to detect suspicious or prohibited activity before their approval. If this process confirms fraudulent or risky behavior, the transactions are flagged. This step in the transaction screening process is crucial for filtering out illicit attempts to avoid regulations, such as sanctions.
In a broader sense, transaction screening validates transaction details to prevent financial crime, such as:
- Corruption
- Fraud
- Terrorist financing
- Weapons proliferation
- Money laundering
- Sanction evasion
Transaction screening is also a crucial part of a company’s fraud risk management within the customer due diligence (CDD) framework, which should:
- Occur before the transaction approval.
- Offer clear risk insights, including both internal and external data.
- Use updated sanctions lists to identify sanctioned entities, locations, and activities.
This process scrutinizes transaction information in order to identify risks in payments before they’re authorized and executed. Financial institutions and other regulated entities should implement transaction screening to comply with local and global AML/CTF regulations.
Related: What is the Difference Between CDD and EDD?
What Makes Transaction Screening Effective?
An effective transaction screening process should use both internal and third-party risk insights. At the same time, a robust transaction screening means that the company is capable of recognizing crucial AML red flags for risks that would help identify and prevent suspicious activities more easily.
Here’s a short list of the top three factors that make transaction screening solutions effective:
- Data quality. Effective transaction screening solutions should incorporate the company’s data and third-party risk information. Often, many screening solutions are AI-powered, which means they are better capable of identifying key red flags for potential risks, helping companies comply with regulatory standards.
- Simple interface. Proper transaction screening solutions should clearly communicate collected data to analysts, enabling them to analyze alerts and escalate the detected suspicious activity promptly. Additionally, such solutions should be customizable in order to fit the company’s unique risk tolerance and compliance policies tailored to their operating industry or business model.
- Integration. Top-notch transaction screening solutions should seamlessly integrate with the company’s entire risk dataset, including compliance and theft data, which helps build an overall effective AML program.
However, regulators typically prioritize a risk-based approach to AML/CFT compliance instead of specifying detailed tools and processes. Nevertheless, transaction screening is a part of any effective program.
What is Considered a Red Flag in Transaction Screening?
Red flags are indicators that prompt further investigation during transaction screening.
These indicators can include suspicious signs, showing that the transaction:
- Involves potential illicit goods, such as dual-use items.
- Is directed to a sanctioned location.
- Is an unusually large amount for the account.
- Contradicts the company’s accepted risk appetite or policies.
- Involves a sender or recipient who is sanctioned or has associated adverse media.
- Involves other parties in the transaction linked to sanctions (such as the beneficiary’s bank).
When compliance specialists detect any of these red flags during transaction screening, they typically move on with a more complex review. Despite that, a red flag isn’t automatically a crime. Sometimes, a transaction is found to be illicit, such as involving sanctioned entities, while other times it may be deemed legitimate after further investigation.
Related: Financial Crime Compliance — Comprehensive Business Practices
Who is Legally Required to Implement Transaction Screening?
Companies that are deemed as financial institutions must comply with AML requirements, that means integrating transaction screening as part of their AML programs.
This includes a wide range of entities such as banks, lenders, real estate agents, investment firms, and other companies, including:
- Cryptocurrency exchanges
- Travel companies
- iGaming platforms and casinos
- Asset management firms
- Brokers and dealers
- Fintech companies
- Luxury item businesses
Keep in mind that the definition of “financial institutions” is fluid and continues to expand globally.
What is Transaction Monitoring?
Transaction monitoring is a process that represents the ongoing surveillance of completed and processed transactions for potential threats. It aims to observe customer transactions by analyzing historical and current customer data in order to gain a comprehensive understanding of customer activity.
Companies use transaction monitoring to scrutinize both incoming and outgoing transactions for signs of fraud after they’ve been processed. During transaction monitoring, companies also often employ some sort of automation in order to check all the transfers, deposits, and withdrawals.
Potential risks that companies can encounter during transaction monitoring include:
- Money laundering
- Terrorist financing
- Sanctions breaches
- Other illicit activities
Advanced transaction monitoring software allows businesses to assess all transaction alerts within the broader context of their risk data. Similarly to transaction screening, accurate and transparent data collection is essential for effective transaction monitoring.
What Does the Transaction Monitoring Process Look Like?
A proper transaction monitoring process enables companies to review all transaction alerts within the context of other risk data. Banks and other financial institutions are mandated to monitor customer transactions to detect potential links to money laundering and other financial crimes.

Monitored transactions typically undergo automatic evaluation against the company’s internal risk assessment rules.
Organizations that conduct transaction monitoring include the following steps in the process:
- Establishing the customer’s risk profile
- Detecting anomalies
- Investigating identified suspicious activity
- Reporting such activity to the authorities
Upon detecting suspicious activity, companies should collect transaction details and submit them through a Suspicious Activity Report (SAR) to the appropriate regulator within a given timeframe. So, naturally, the transaction monitoring process helps avoid unwanted consequences, including tarnishing a company’s brand and reputation, which often leads to customers seeking alternatives from competitors.
What to Look for in a Robust Transaction Monitoring Solution?
An effective transaction monitoring solution should seamlessly track and monitor past transactions, ideally in real-time, and incorporate additional risk data, such as transaction screening or previous investigation data.
A robust transaction monitoring solution helps analysts assess risks and answer key questions:
- Is the customer initiating a transaction with a recipient classified as high-risk, such as someone on a sanctions list, watchlist, or a politically exposed persons (PEPs) list?
- Does the transaction surpass record-keeping thresholds (for example, the $3,000 threshold for payment orders in the United States)?
- Where is the transaction originating from? Are either of the locations considered high-risk by regulatory bodies like FATF?
- Has the customer significantly increased their spending within a short timeframe, such as in the past hour?
- Is the customer conducting multiple transactions below the reporting threshold, a practice known as smurfing or structuring in money laundering?
However, compliance specialists can handle alerts more effectively when they can assess them within other crucial aspects of the risk management system. This includes company data associated with the Know Your Business (KYB) process, as well as customer Know Your Customer (KYC) data and gathered transaction screening information.
The Difference Between Transaction Screening and Transaction Monitoring
Transaction screening reviews transactions before approval, while monitoring evaluates transactions that have already taken place. Once a transaction is flagged, compliance specialists assess the flagged transaction to determine its legitimacy and decide whether additional investigation or reporting is necessary. Both processes aim to identify suspicious and unusual factors warranting further investigation.
For example, during transaction screening, payments for illegal items may be declined, regardless of the customer’s past behavior. During transaction monitoring, while individual transactions may seem low risk and pass screening, they could be part of a larger network of questionable behavior. This connection to previous transactions analyst teams to continue the monitoring process.
Related: Screening and Ongoing Monitoring — Using AI for AML Compliance
The Importance of Transaction Screening and Monitoring
Financial institutions must ensure they have robust transaction screening and monitoring processes, mostly due to one ultimate reason: legal compliance. Despite that, remaining in line with the law isn’t the only reason why both procedures are important. Through transaction screening and monitoring, businesses can detect various threats and report illicit activities while protecting customers from fraud.
Effective transaction screening and monitoring can:
- Boost corporate performance.
- Enhance the end-user experience.
- Help businesses comply with regulatory requirements.
- Improve the client’s experience and foster customer loyalty.
- Enhance the effectiveness of the company’s AML/CFT program.
Financial institutions can mitigate risks by promptly flagging and reporting suspicious transactions, enabling necessary actions to be taken.
Neglecting to screen and monitor transactions or submit required reports promptly can result in major consequences. For example, regulators may impose fines and legal actions against both the institution and its responsible individuals. So, to ensure proper AML compliance, it’s vital to integrate both processes into dependable datasets, enhancing risk management practices.
Related: What are the Five Pillars of AML Compliance?
Screening and Monitoring in the Context of AML Compliance
Constantly monitoring, maintaining, and improving transaction screening and monitoring systems is essential for the company to comply with ever-evolving AML regulations. This includes updating AML software automation rules and parameters to address emerging risks, as well as regular system and performance evaluations.
Moreover, financial institutions need to assess the money laundering risk associated with each customer. They do this by verifying customer-provided information (such as name, date of birth, etc.) against authoritative databases, including watchlists, adverse media and PEPs and sanctions lists, as well as other types of reports.

To evaluate its screening and monitoring processes, companies should answer these questions:
- Does the system prioritize alerts effectively, especially with AI-enhanced tools?
- Are manual tasks causing risks to be overlooked?
- Do both processes use relevant data and provide accurate information for alerts while prioritizing the riskiest ones?
- Does the system quickly access updated sanctions data?
Businesses should select a tool for transaction screening and monitoring aligned with their risk-based approach and capable of managing diverse customer and transaction types.
At iDenfy, we have the complete toolkit for your compliance needs — AML screening, ongoing monitoring and transaction monitoring solutions that require minimal effort to set up, including custom rule generation, report download options, technical integration support, and much more. Get started today.