How do you know your customers? Whether a new customer is making a purchase, submitting an application, or engaging in any activity requiring a certain level of authentication, identity proofing comes into play.
Verifying your customers and conducting identity checks isn’t just about compliance and regulations anymore. To prevent fraudulent activities, companies must find an efficient way to confirm that the person interacting on the other side of the screen is indeed who they claim to be.
Previously, customers often had to send a physical form of identity documents for verification purposes. However, with artificial intelligence, biometrics, or selfie verification, the process of identity verification and identity proofing has become much more user-centric.
Find out what identity proofing is exactly and how to make this process secure without disrupting the end-user experience.
What is Identity Proofing?
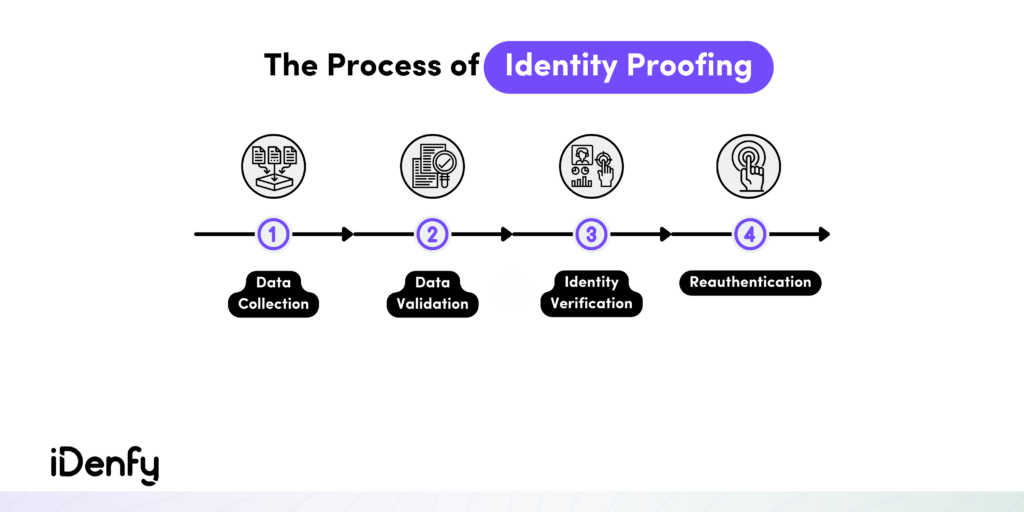
Identity proofing is an identity verification process that’s designed to establish the authenticity of an individual’s claimed identity in online transactions.
The National Institute of Standards and Technology (NIST) describes identity proofing in its Digital Identity Guidelines by providing its two key stages:
- Claimed identity. This refers to the information a user provides when registering with an Identity and Access Management (IAM) system, essentially who they say they are.
- Actual identity. This refers to the data that shows the actual authenticity of a user’s identity, essentially who they truly are.
The overarching objective of identity proofing is to establish a match between a user’s claimed identity and their actual identity. It goes beyond traditional authentication measures, such as usernames or passwords. Typically, this process is implemented either during the customer onboarding process or as an additional security layer alongside the traditional verification measures.
That’s because using traditional methods, such as knowledge-based questions, isn’t the most secure form of identity proofing. Another person could potentially provide the required information. So, today, we have more robust options — automated identity verification solutions that encompass additional requirements, such as age verification or phone verification.
How Does Identity Proofing Look in Practice?
The most popular identity proofing solution in various industries, including financial services, crypto exchanges, and others, like real estate, is document verification. Companies often combine it with biometric measures, such as a video liveness check or a selfie photo verification. This way, they can be assured that the user is really who they claim they are.
Identity proofing is more than collecting personal information from your customers. As a business, you’re responsible for ensuring that the collected data is legitimate. That means you must detect stolen identities and fake documents and deter any type of fraud before giving criminals access to your platform. At the same time, legitimate customers need to be checked in a simple and timely manner.
That’s why, in practice, identity proofing solutions, such as biometric verification, should match customers’ expectations by prioritizing a seamless user experience. Businesses who want to stand out in the market choose solutions with:
- Intuitive interfaces,
- Clear instructions, and
- Minimal steps to ensure that users can easily navigate the process.
Typically, companies use biometric verification, such as facial recognition, to integrate into the Know Your Customer (KYC) verification flow. This makes the whole identity proofing process both convenient and secure. For complete accuracy, some third-party providers also offer manual identity verification, where real KYC agents review each identification to double-check the AI software’s accuracy.
📎 Related: How to Improve KYC Verification? Tips For a Frictionless User Experience
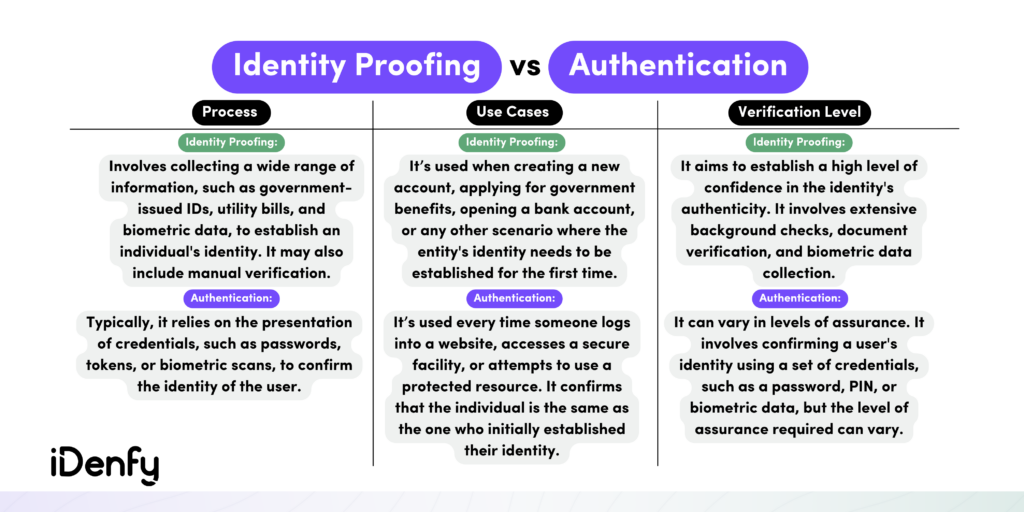
What is the Difference Between Authentication and Identity Proofing?
Authentication is the process of verifying that an individual or entity is indeed who they claim to be. It’s typically used at the point of login or when accessing a secured resource. In contrast, identity proofing is a broader process. In other words, identity proofing and authentication serve the same purpose of verifying a user’s identity, but the crucial distinction lies in when these checks happen.
A well-recognized use case for both authentication and identity proofing is when users want to access their bank accounts. These are the stages they would need to go through:
1. Identity Proofing for Customer Onboarding
Identity proofing primarily occurs during onboarding or when establishing a user’s identity in a new relationship. That’s because KYC regulations oblige banks and other financial institutions to confirm and validate their customers’ identities — or conduct identity verification.
According to the FATF recommendations, you should pay attention to these red flags surrounding customer behavior and KYC compliance:
- Establishing multiple accounts using different names.
- Initiating transactions from untrusted IP addresses.
- Providing incomplete or inadequate identity information.
- Rejecting requests for identity proofing or source of funds inquiries.
- Submitting counterfeit or fabricated identity documents or photos.
- Having customers who are flagged on watchlists.
- Frequent changes in customer identification details.
2. Authentication for Returning Customers
In the meantime, authentication is employed when a user returns. That means authentication’s goal is to ensure that the user requesting access is indeed the same individual who initially established the relationship, maintaining ongoing security.
So, later during the customer cycle, the customer might be asked to re-authenticate their identity due to a higher-risk situation, which is also governed by Anti-Money Laundering (AML) regulations. For example, if a customer intends to surpass the $10,000 threshold in a transaction, they will be required to reconfirm their identity before proceeding with the transfer.
Depending on your risk mitigation strategy and the specific customer, you may also want to keep an eye on the following risk factors:
- Unusual spikes in customer activities.
- Cross-border activities that are out of the ordinary or occur in unfamiliar regions.
- Involvement of individuals listed on sanction lists.
- Mentions in adverse media.
Which Sectors Require Identity Proofing?
Identity proofing enhances security by ensuring that your platform only grants access to legitimate users. However, it’s important to note that identity proofing may not be needed in every situation. If you only need to monitor users who are already well-known within your organization, such as employees accessing internal systems, identity proofing might not be necessary.
Nevertheless, when you must be certain of user identity across a large user base, identity proofing becomes crucial. For instance, it is vital in securely onboarding patients for their healthcare services or facilitating secure fintech and e-commerce services. In other words, if your business handles sensitive or regulated information, you’ll need to implement identity proofing.
Here are other examples in more detail:
- Sharing economy platforms. The sharing economy relies entirely on online interactions, making the issue of identification a significant challenge. That’s why companies in the sharing economy, like ride-sharing and home-sharing services, require identity proofing solutions to ensure safety for both users and providers.
- Cryptocurrency exchanges. Due to the potential for financial crimes and fraud, cryptocurrency exchanges often implement strict identity proofing measures to comply with AML and customer due diligence (CDD) requirements.
- Telecommunication companies. Telecom providers use identity proofing to activate phone lines, prevent fraud, and comply with regulations. Furthermore, AI-driven identity proofing solutions empower telecom operators to evaluate client risk by conducting various identification checks, including face matching that incorporates 3D liveness detection and anti-spoofing technology.
- Legal service providers. Lawyers and solicitors must strictly adhere to KYC regulations to ensure that they offer their legal services exclusively to authentic clients. For example, notaries also require identity proofing to verify the identities of clients, witnesses, and signatories for legal documents and transactions.
- Financial institutions. Banks, credit unions, and other financial organizations require robust identity proofing to comply with KYC and AML regulations. They need to verify the identities of customers for account opening, transactions, and overall fraud prevention.
📎 Related: What is a Risk-Based Approach to AML?
Identity Proofing Examples
If you want to streamline your onboarding processes, identity proofing is a crucial measure to safeguard both your business and your users from fraudsters.
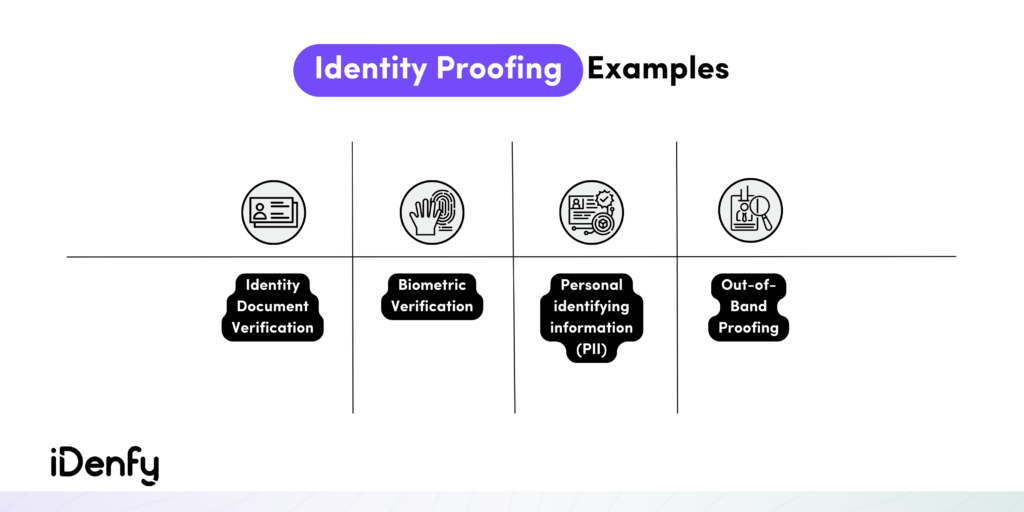
For more context, here are the most common examples of identity proofing:
Document Verification
Document verification is the process of confirming the authenticity of a document, which could be anything from a bank statement and employment record to a business document and more. Users may be requested to undergo identity proofing to provide additional verification of their claimed identity, such as disclosing their name and providing a government-issued document like a photo ID.
To access the information contained within the document, the data needs to be extracted. Companies carry out this extraction process through various methods, such as optical character recognition (OCR), pattern recognition, and other techniques.
You should answer these questions when conducting document verification:
- Are all required pages of the document uploaded, especially if it consists of multiple pages?
- Is the document’s edge unaltered and not cropped or tampered with?
- Are all watermarks, holograms, stamps, foils, fonts, and textures in place?
- Do the color, lighting, or shadows show any signs of forgery?
It’s essential to recognize that identity documents can be subject to theft, tampering, or fraudulent creation by malicious actors. Therefore, only checking an image of a photo ID is insufficient as definitive proof of that person’s true identity. That’s why numerous businesses incorporate document verification as a component of their comprehensive identity proofing procedures alongside other verification methods, such as selfie checks or additional manual verification checks.
📎 Related: How to Spot a Fake ID and Protect Your Business from it
Biometric Identity Verification
Biometric identity verification involves identifying users by their distinct physical characteristics, such as their face, fingerprints, or voice. Such solutions provide a higher level of assurance when it comes to identity proofing. That’s because they are safer than other verification methods like usernames and passwords.
Businesses choose to implement biometric identity verification due to these benefits:
- Accuracy. Traditional methods, such as knowledge-based questions, may be susceptible to human error during the verification process. Biometric systems reduce this risk by relying on automated and precise measurements.
- Convenience. Biometric ID verification is also more convenient than traditional identity proofing methods because users don’t have to remember a password. They just need their own face.
- Security. Biometrics are difficult to fake, steal, or misplace, making it less likely for fraud or identity theft to occur.
For example, combining biometric verification with facial recognition technology and adding the document verification of a government-issued photo ID can help you effectively detect fraud attempts, including stolen or synthetic identities. This method of identity proofing is the most dependable in the market because when you show your government ID, you also have to take a selfie or a short video with your device’s camera to confirm that you’re the same person.
Personal Identifying Information (PII)
Personally identifiable information, or PII, encompasses data that can be used to identify someone. This includes direct identifiers like their name, address, Social Security Number (SSN), and contact details, as well as indirect identifiers like gender, race, and birth date when used in combination with other data elements.
In the context of identity proofing, a company can request information that only the user should know, such as their SSN. However, the PII method has some drawbacks. For example, hackers who purchase leaked data might use it for fraudulent purposes. As a result, since we now have modern verification solutions, PII is not the most secure way to verify someone’s identity.
Out-of-Band Authentication (OOBA)
Out-of-band authentication (OOBA) is a verification measure that uses a different communication channel for verifying a user compared to the one used for signing in or conducting a transaction. OOBA is commonly referred to as a type of two-factor authentication (2FA) or multi-factor authentication (MFA).
Here are some use cases of out-of-band authentication for identity proofing:
- Employing biometric readers for fingerprint scans or facial recognition.
- Conducting phone calls for voice authentication.
- Using QR codes containing encrypted transaction data.
- Sending push notifications to mobile devices.
For example, OOBA is when the user first enters their username and password and then provides a code sent to them via email or SMS for additional confirmation. It adds an extra layer of security by confirming identity through an independent channel, reducing the risk of fake identities or impersonation.
Get Started with Automated Identity Proofing
Today’s users expect quick onboarding processes. Manual identity proofing is challenging to scale for systems or websites that handle a high volume of access requests. That’s why traditional identity proofing measures can negatively affect user experience. When users encounter too many steps to create an account, they will likely abandon your platform.
By implementing iDenfy’s full-stack identity verification solution, you can build a robust identity proofing system without adding unnecessary friction to the user experience. Ultimately, this helps you reduce the need for manual work and accelerate a secure, fraud-free journey for the end user.
Drop us a message for more info about our KYC/AML hub.