Email verification means that the user needs to provide a valid email address, then receive a one-time password (OTP) to their inbox, enter it as a way to approve that this identifier is correct and then link it to their account details or continue to the next Know Your Customer (KYC) verification step. That’s why it’s considered to be one of the most basic yet fundamental identifiers in this digital era. From a fraud prevention perspective, verifying an email address is much safer than only accepting standard credentials, such as a username and password.
More importantly, this step in the KYC onboarding process is typical, so it provides a sense of security and familiarity, making the end-user experience smooth and simple. An invalid email address might seem like a tiny detail, but it can actually signal fraudulent behavior, such as an attempt to bypass registration with fake personal details. Ultimately, by adding email verification, you ensure that only genuine users move forward and access your services while detecting risks early.
But is it really that simple, and what else do you need to know about email verification? In this guide, we break down what it means in practice and share concrete use cases that highlight how verifying emails can help improve your fraud prevention strategy.
What is Email Verification?
Email verification is a security measure designed to add an extra authentication layer via one-time passwords (OTPs) sent to the users’ email inboxes. Once the user receives the code, they are asked to enter it and, in this way, approve that the email address is valid and belongs to them. This not only improves identity verification but also reduces fraud risks linked to fake or unverified users.
That’s why email verification helps:
- Check if the email’s syntax is correct and that the domain is active.
- Assess if the user’s mailbox can actually receive messages.
- Verify if the user is reachable and real, and not just an account used for fraud.
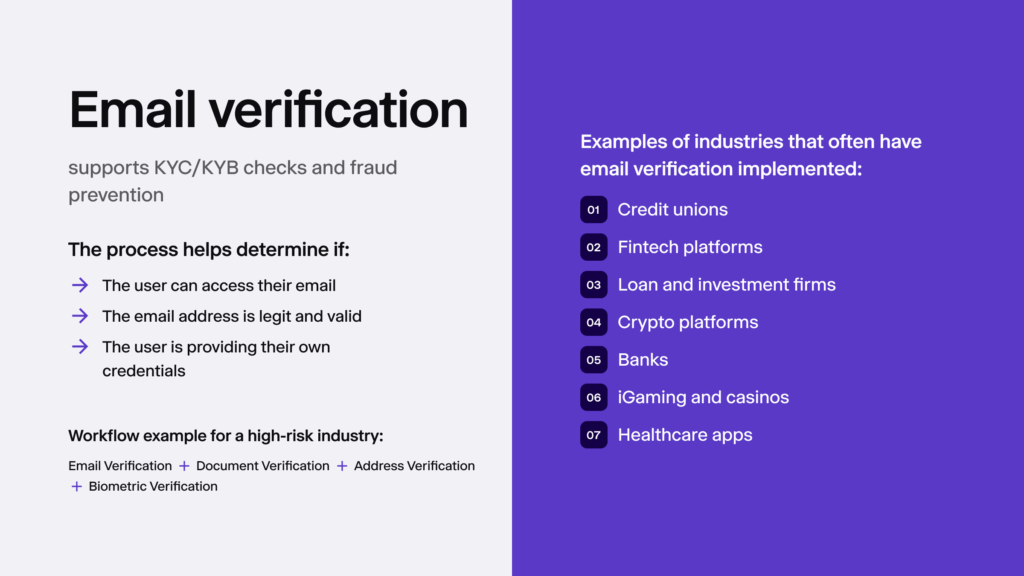
In KYC verification or identity verification for user onboarding, email verification is often used next to other verification measures in regulated sectors (like fintech) designed to assess and approve a user’s identity, such as document verification, where the user is asked to upload their passport, driver’s license, or ID card. This helps collect extra information about the user and identify high-risk customers right from the start.
Depending on your workflow, you can allow the user to retry and verify their email address a few times (if they enter a wrong authentication code) or block them from moving on to the next step during the registration process.
Related: What is KYC Onboarding?
How Can Users Complete the Email Verification Process?
Email verification is backed by a fully automated process, which is often incorporated into a bigger onboarding workflow with KYC checks like ID document verification and biometric verification. The process validates the ownership and accuracy of a user’s provided email address.
Often, to pass this check, the user is required to:
1. Provide Login Details and a Valid Email Address
The email verification process is the first step in the onboarding flow and begins by asking the user to submit their credentials (which are often their username and password) and email address.
The user’s address in this case is important because it’s later used as a communication channel for marketing purposes or in cases when the account needs to be confirmed again via an OTP code in the email as part of reverification (for example, before a high-risk, atypical, large transaction on an online marketplace).
2. Receive a One-Time Code in the Inbox
A unique one-time password (OTP) is automatically generated by the system and sent to the provided email address. This ensures that the user has access to the email that they claim to own. So, for example, if a person tries to bypass the system and enter an invalid email, they won’t receive the passcode, and their account won’t be created or allowed access to the services they’re trying to reach.
3. Enter and Verify the Code
The user checks the received password and enters it on the company’s site or application. There are a few outcomes here. If the code’s correct, the user passes, and their email is verified, they get the green light to move to the next step or finalize their account creation process. If they don’t enter the code, it expires, and they aren’t forwarded to the next verification step. Depending on the platform and its risk assessment policies, this can be treated as a sign to reject the user’s application altogether or allow them to reattempt the verification.
Sometimes, the user is also allowed to choose another alternative method, such as SMS verification, which is based on the same principle, but in this case, the OTP is sent to the user’s phone via SMS.
4. Proceed with Onboarding or Additional Checks
Once the email is verified after the user enters the code, the system either grants the user access to the platform or directs them to the next verification steps, depending on the regulatory requirements, the operating country, the industry, and the platform’s particular use case.
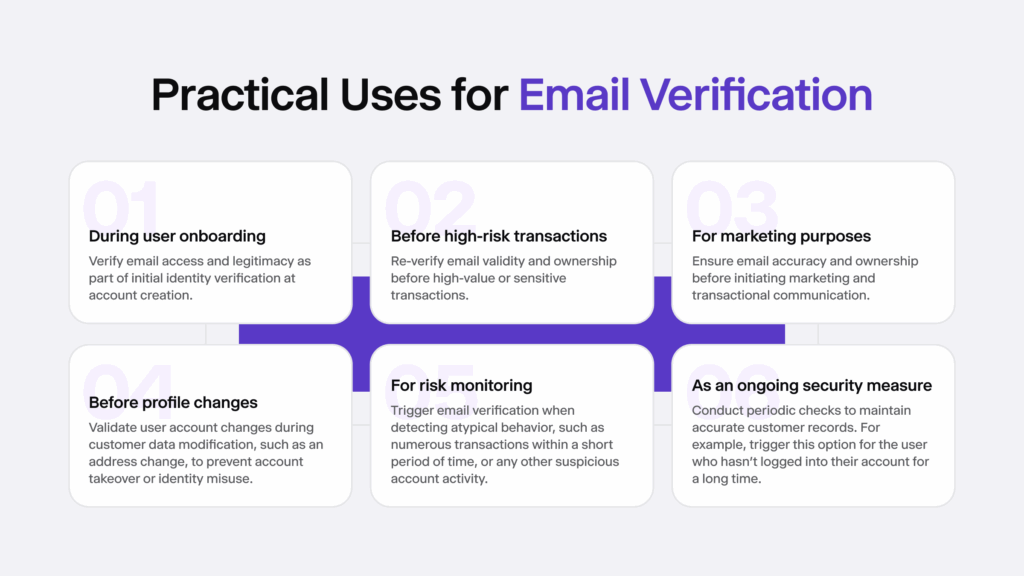
For example, loan service providers will have extra checks, such as Source of Funds (SOF) verification, while e-commerce marketplaces will have fewer verification steps in place due to general KYC and Anti-Money Laundering (AML) requirements that affect the user onboarding flow, unless they sell age-restricted items that are catered to an adult-only audience, requiring age verification.
Additional KYC Checks After Email Verification
Common examples of possible identity verification measures include:
- ID document verification. This includes verifying government-issued IDs such as passports or driver’s licenses to confirm the user’s identity. Often, OCR technology is used to automatically extract personal details from the document, making the whole process fast and user-friendly.
- Biometric verification. This includes using facial recognition technology and liveness detection to ensure the user is physically present and that their facial features match the photo on the ID.
- Proof of Address (PoA) verification. This confirms the user’s residential address through common PoA documents, such as a utility bill or a bank statement.
- Bank account verification. This includes verifying the user’s IBAN by collecting information from their bank after they are asked to log in to their account. Due to open banking capabilities, the system, such as iDenfy’s solution, automatically assesses transactional history and determines the risk score linked to the user’s financials.
In more advanced cases, companies use various fraud prevention measures on top to assess risk signals in the background. For example, solutions like phone number verification can determine if a user’s provided phone number was previously linked to crime and if its carrier country is a high-risk location. A similar tool, for example, iDenfy’s Proxy Detection, can detect fraudulent proxies, VPN use, and even links to the back market, providing a user’s risk score automatically (categorizing them from low to high risk).
Related: AI in Fraud Prevention
Which Industries Often Implement Email Verification?
Sectors that use email verification for user onboarding and fraud prevention include:
- Banks, credit unions, and fintech providers
- Virtual asset service providers (VASPs)
- Online casinos, sports betting operators, and lottery platforms
- Insurance firms, securities brokers, and lending institutions
- Luxury goods dealers, auction houses, and high-value marketplaces
- Notaries, accountants, auditors, and independent legal advisors
- Real estate firms that use layered verification, including email, to screen buyers and tenants
What are the Main Types of Email Verification?
There are three main types of email verification that can be combined with other KYC methods or used separately alone:
1. Email Access Verification
This includes verifying that the user can enter their email inbox. This can be done by sending an OTP, which is often a four or six-digit code, or via a verification link, similarly to how iDenfy has its Magic Link feature for standard identity verification.
2. Email Ownership Verification
This means that the user is also going to be checked if they are the ones registering with the email address that belongs to them, and the account isn’t being created under a fake or stolen identity (with a stolen email address, through phishing, for example). However, this often works best with an extra KYC process during the same onboarding, for example, an ID document check.
3. Email Reputation Verification
This involves assessing the email in a more detailed way to determine its risk level through tailored risk assessment factors, similar to how a phone number’s risk can be evaluated (based on factors, like if it’s coming from a high-risk country). This type helps verify the email’s history while determining suspicious red flags, such as links to fraudulent domains.
Related: Top 5 Identity Verification Measures
Why is Email Verification Important?
Verifying your customers’ email addresses helps detect indicators of fraud and ensure only genuine users move forward in the verification process. Fraudsters often use disposable, fake, or simply the same email addresses for multi-accounting, bonus abuse, or bypassing platform rules. By verifying customer emails at the onboarding stage, businesses can prevent bots, spammers, and any deceptive users with a low intent of actually fairly engaging with the services they are claiming to be registering for.
In this sense, email verification works like a first line of defense (even if a stricter KYC workflow follows afterwards) for reducing abuse and ensuring compliance with platform policies.
What are the Benefits of Email Verification for Fraud Prevention?
The biggest benefits that make email verification an effective fraud prevention solution are:
- Smooth, user-friendly onboarding flow. The customer only needs to go through a few steps that are fully automated, requiring minimal, low-friction input from their side.
- Protection against unauthorized transactions. Requesting to verify an email through an OTP, for example, before a high-value transaction or when an AML red flag is detected, adds an extra layer of security.
- Identification of various fraud types. Since email verification is the first step in the onboarding flow, it helps detect risks and identify potentially malicious users right from the start. This includes cases when a synthetic identity is used or when a person is attempting to take over another account that doesn’t belong to them.
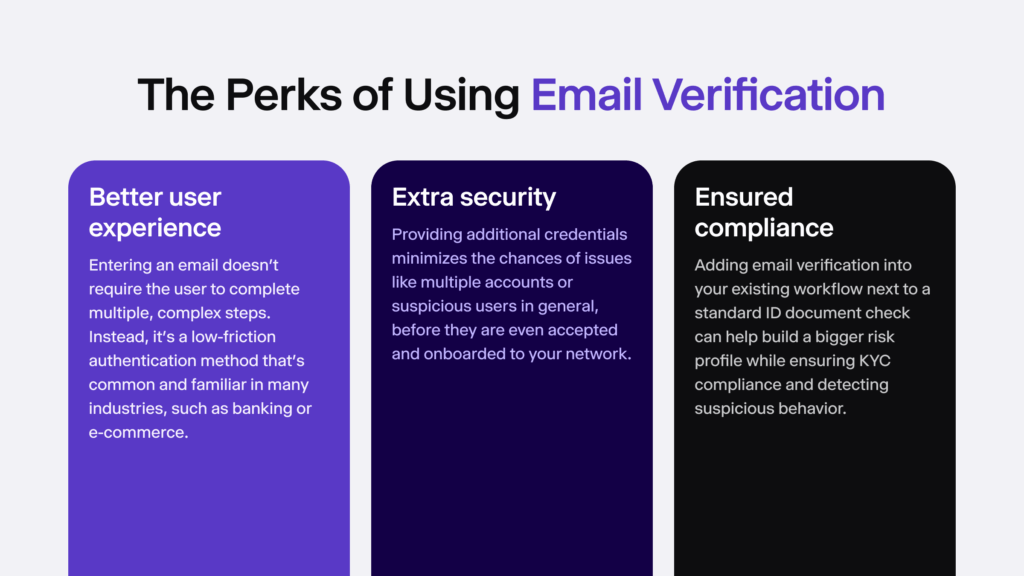
With additional KYC measures on top for use onboarding in regulated industries, email verification is a good, cost-effective solution to automate onboarding and ensure compliance at the same time.
How Does iDenfy’s Email Verification Solution Work?
The process is simple for end-users, as they’re asked to:
- Enter their email address
- Check their email inbox to access the six-digit OTP
- Enter the code to confirm it
- Proceed with other ID verification steps (that can differ, depending on the generated workflow)
You can activate this feature with a single click using iDenfy’s dashboard. This no-code email verification solution also works for Know Your Business (KYB) onboarding, along with other custom features, such as extra PoA checks and Bank Verification, or tailored questionnaires that help automate access to certain data collection channels that don’t go into the provided pre-made templates that are available for certain industries (for example, fintech clients).
➡️ iDenfy also provides SMS-based OTP verification, or SMS verification, enabling businesses to confirm phone numbers as an additional first-step onboarding measure.
Where Can I Use iDenfy’s Email Verification?
Automated extra add-on services, such as iDenfy’s email verification solution, can increase conversions and onboard more genuine users in less time, saving you costs on KYC onboarding and removing the hassle of managing and manually assessing personal details. The software is multi-functional, meaning it can be used in various industries and customized by adjusting the strictness of the identity verification workflow.
With iDenfy, you can use email checks with identity document checks or create a fuller flow with biometric or database verification, such as TIN/EIN verification, SSN verification, criminal background check, and more, depending on your risk appetite.
For example, most businesses use email verification to:
Improve KYC Onboarding with Verified, Genuine Emails
This is vital in regulated industries. Collecting and verifying a user’s email address not only helps with the initial onboarding process but also ensures ongoing due diligence (ODD) and helps with reverification where personal information needs to be confirmed again and verified before high-risk scenarios or in cases when the user simply wants to change an email address linked to their account. This helps avoid account takeovers and fraudulent sign-ups.
Ensure KYB Compliance By Verifying Partners and Vendors
As part of KYC and AML compliance obligations, email verification helps confirm that addresses are active, reputable, and tied to both real individuals and other companies. This process supports both B2C and B2B onboarding, helping companies improve their third-party risk management strategies to prevent money laundering and other financial crimes that can happen through vendors. This is part of the KYB, or Know Your Business, compliance framework, which requires assessing risks linked to other businesses to determine whether they are a compliant and suitable partner before granting access to financial operations or moving forward with a business relationship.
That’s why deconstructing a potential partner’s or service provider’s corporate structure and requiring directors or shareholders to complete a proper KYC check, with the added email verification step, helps your company prevent sanctions breaches and other non-compliant, fraudulent activities. This process often uncovers shell companies that are used for fraud, hidden ownership structures that raise many red flags, money mules, and other money laundering techniques commonly used in B2B channels.
Related: Know Your Vendor (KYV) Guide
Guarantee Transparent Communication and Audit-Ready Data Trails
Email verification in KYC verification also secures communication channels by ensuring transaction alerts, password resets, and compliance notices are reliably delivered. This not only reduces operational risks but also ensures legal traceability for audits and regulatory reporting. All personal data, verification denial reasons, and related KYC profile details are stored in one dashboard, strengthening trust and ensuring accurate records for oversight.
This is also very useful for Enhanced Due Diligence (EDD). For example, when a suspicious transaction or user activity needs to be assessed and reported through a Suspicious Activity Report (SAR), if it’s not a false positive. In cases like this, iDenfy’s software offers additional AML screening and real-time monitoring, while also helping you maintain an AML-ready audit trail. iDenfy is ISO-certified and complies with the GDPR and other data protection regulations.
Related: What is the Difference Between CDD and EDD?
Final Words
It’s safe to say that with a no-code email verification integration, businesses can combine OTP email authentication with additional ID verification and stricter compliance checks seamlessly, without complex development. While this step might seem minor, it is a powerful tool against multiple accounts and fake identities that are used for fraud online. Basically, any platform that has monetization and handles financial transactions is at risk. By adding email verification before standard ID document checks, you can block fraud attempts early.
For regulated industries, iDenfy helps build a fuller email verification workflow with extra KYC checks, KYB onboarding solutions, and additional AML screening — all within a centralized dashboard to ensure security, efficiency, and full regulatory compliance. Interested in seeing how this all looks in action? Try out for free today.