Companies are responsible for monitoring financial transactions and reporting suspicious activity, which is the starting point for tracking fraud, money laundering, and other criminal financial activities. ACAMS and Thomson Reuters did a recent study in which anti-money laundering (AML) professionals expressed concerns about proper fraud monitoring due to increasing workloads.
This happens to many companies that have high transaction volumes. The amount of data and the growing customer base can lead to an increasing number of fraudulent activities. However, there are many factors that make up this puzzle. Simple things like the lack of a compliance culture in an organization can lead to poor AML process management, which is vital to ensure proper AML fraud detection and prevention.
While it seems common knowledge not to neglect risk assessment protocols and ensure complete compliance with AML standards, many companies still struggle with it. For example, it’s crucial to know who you’re doing transactions with and where their funds come from, especially in high-risk transactions or when dealing with individuals at higher risk of corruption, such as Politically Exposed Persons (PEPs).
So, how big of an issue money laundering and financial crime is today, and how can companies prevent AML fraud and other financial crime from getting involved in their space — we break these and more questions down below.
What is Anti-Money Laundering (AML)?
Anti-money laundering (AML) is a set of laws and regulations designed to help companies build processes to detect money laundering activities and other cases of financial crime. AML compliance consists of screening, monitoring, and reporting suspicious activity and is a bigger picture of other related procedures, such as Know Your Customer (KYC) or customer identity verification.

Companies use AML compliance processes in order to:
- Detect fraud and protect their customers
- Avoid non-compliance penalties and reduce costs linked to fines
- Comply with AML regulations and minimize chances of criminal activity
AML is closely related to the counter-financing of terrorism (CFT). Financial institutions and other regulated entities use both regulatory compliance approaches to combat the movement of illicit funds. That’s because AML compliance addresses the source of funds, while CFT compliance focuses on their destination.
The Cost of Money Laundering
Thomson Reuters reports that the past decade hasn’t been the best for banks in terms of non-compliance. Regulators in Europe and the US have imposed $342 billion in fines on banks for AML compliance violations since 2019. Another notorious example is the $184 million penalty imposed in 2017 by FinCEN on a money service business (MSB) for failing to maintain an effective AML program and delaying suspicious activity reports (SARs).
In general, the cost of money laundering remains an issue globally. An estimated $800 billion to $2 trillion is laundered annually due to businesses unwantedly becoming financiers for money launderers, terrorist networks, drug cartels, and other criminal groups.
Related: What is an AML Compliance Program?
What is AML Fraud?
AML fraud is the process of illegally laundering money through a company’s products or services, no matter its industry, location, and other factors, since fraudsters typically use any opportunity and regulatory compliance loophole to clean dirty funds.
To minimize chances of AML fraud, companies:
- Conduct internal risk assessments to identify and report on their exposure to AML fraud.
- Establish and execute strategies to adhere to AML/CTF laws.
- Collaborate with regulators and auditors to mitigate money laundering risks for their business.
In general, money laundering involves hiding the origins of money obtained through crimes such as human trafficking, terrorism financing, drug trafficking, tax evasion, or corruption. However, while all forms of money laundering are against the law, AML fraud particularly focuses on cases when criminals try to bypass AML controls to launder illicit funds. Often, they either do it directly or through money mules.
An Example Showing How AML Fraud Works
Money laundering is all about criminals using fake or hidden identities to sign up for new accounts and launder money. Dark web marketplaces are a good example of how AML fraud and money laundering work. For example, due to the widespread use of digital assets and the anonymity that cryptocurrencies offer, many criminal-oriented marketplaces offer money laundering services for their clients.
There are on-chain mixers that help fraudsters mask illicit funds by obscuring blockchain transactions. Mixing or tumbling means blending transactions across multiple cryptocurrency exchanges to obscure their traceability to any specific exchange or account.

Fraudsters also use gambling platforms to deposit funds. In this case, the illegal money is cashed out or used in coordinated bets with affiliates. More traditional AML fraud methods include shell companies or offshore accounts that are also used to hide the origins of fraudsters’ money. Other fraudulent schemes, such as smurfing, are employed as well, making tracing and prosecution more complex.
So, no matter if the industry is high-risk or not, there’s a chance that the business can unintentionally overlook falsified information or accept stolen identities, especially if they lack AML automation in their screening and monitoring practices or lack reliable document databases.
What is KYC in the Context of AML Fraud Prevention?
In the context of preventing AML fraud and money laundering, regulatory compliance starts with Know Your Customer (KYC). It’s the process of verifying customers’ identities, often during the onboarding process, with the intent to detect fake ID documents and assess whether the user’s money is coming from legitimate sources.
Money laundering has three primary stages, which consist of:
- Depositing illicit funds into the financial system.
- Layering the funds, which consists of multiple transactions designed to obscure the illegal origin of the funds.
- Integrating the money or “washing” the funds by investing in real estate, luxury goods, stocks, and other assets.
The concept of KYC and fraud detection traces back to the 1970s, the Bank Secrecy Act (BSA) in particular. It was initially established to mitigate the risks of money laundering, financial terrorism, and other illicit activities. To this day, KYC compliance focuses on preventing money laundering at the initial stage, when customers attempt to deposit funds, becoming a critical component in AML compliance as well.
Fraudulent Schemes that Criminals Use to Bypass KYC Checks
Criminals have the same goal. That is to find new loopholes that would help them seamlessly integrate dirty money into the legitimate financial system. One of the initial methods to actually achieve this objective is to find a way to avoid detection and, naturally, bypass identity verification.
This is a common practice in jurisdictions where AML laws have loopholes or in areas where security is less of a priority than user experience. Industries where ultra-fast onboarding with minimal checks make it easier for fraudsters to use stolen IDs to quickly open multiple accounts, also known as money mule accounts designed to launder funds.
Fraudsters often use these fraudulent methods during KYC checks:
1. Fake ID Documents
Fraudsters fake identity documents by initiating data breaches using phishing to fabricate data and using it to forge documents. Fake ID documents are designed to mimic a real identity or invent entirely fictitious ones that exist only in theory. Some criminals upload stolen ID documents on the dark web, sometimes in bulk and for very cheap. These are often advertised as complete packages for opening new accounts online, often in neobanks where KYC checks are less stringent.
Related: How to Spot a Fake ID & Protect Your Business
2. Dormant Accounts
Fraudsters sell packages of dormant accounts on the dark web as well. This includes various payment service accounts and other financial accounts that have already been approved by the financial institution. That means the KYC check has already been passed. To achieve this, criminals take over accounts from legitimate holders or collaborate with insiders to gain access, sometimes using accounts of deceased senior citizens.
Because the account already exists, fraudsters can avoid the strict checks that new accounts undergo. That means dormant accounts enable criminals to integrate dirty money into the financial system more easily. To minimize the risk of this sort of crime, companies use reverification measures that are applied throughout the whole business relationship and not just at the onboarding stage.
Related: Account Takeover (ATO) — Meaning, Examples, and Fraud Prevention Tactics
3. Synthetic Identities
Synthetic identities are known to have caused financial institutions trouble over the years. That’s because they are created by combining real and fake data, making it hard to trace them. Criminals use these identities to defraud businesses, exploit promotions, make purchases, launder money, and, of course, bypass KYC checks. Some criminals go to the extent of using stolen ID details from children with clean credit records. This enables them to take out loans and buy, for example, real estate successfully.
What is CDD in the Context of AML Fraud Prevention?
Customer due diligence (CDD) is the process of conducting screening and background checks in order to determine their risk level before onboarding and for the ongoing business relationship with the customer. CDD is part of both AML and KYC compliance initiatives and involves keeping accurate and up-to-date records of transactions and customer data.
CDD measures are backed by the risk-based approach, which has three CDD levels:
- Simplified due diligence (SDD)
- Customer due diligence (CDD)
- Enhanced due diligence (EDD)
Since customer risk profiles can change over time, ongoing CDD measures are very important. Customers may be added to sanctions or watchlists, as well as receive the PEP status, requiring more stringent checks for regulatory risks and compliance issues.
Related: What is the Difference Between CDD and EDD?
Customer Due Diligence Requirements
A typical CDD process consists of three stages: identifying and verifying customers, understanding the purpose of the business relationship, and monitoring and reporting suspicious activity.
In practice, to complete CDD requirements and comply with AML laws, companies implement these steps:
- Collect customer information. Customers’ full name, photo of their government-issued ID, address, tax ID, phone number, email.
- Gather business data for corporate clients. This means identifying information about the client’s business model, source of funds, and beneficial ownership.
- Determine customer risk profiles. This often happens based on three factors (identity, location, and type of business), which indicate their money laundering risk. High-risk customers often require EDD measures as opposed to low-risk users.
- Conduct ongoing monitoring. This means monitoring customers and their transactions with a focus on high-risk users and possible changes in customer profiles after the initial onboarding stage to ensure ongoing due diligence.
CDD measures help prevent complex money laundering tactics like structuring, where larger transactions are broken into smaller ones above the reporting threshold to avoid detection. By conducting internal risk assessments and performing thorough CDD processes, even non-regulated entities can attract new customers and gain a competitive advantage in the market.
What are the Key Challenges of AML Fraud Detection?
The increasing complexity of payment methods, like virtual currencies or prepaid cards, and the cross-border nature of transactions require constant monitoring. In terms of AML fraud detection, this is a complex task because even with automated AML solutions, businesses need compliance staff and constant training to keep up with the regulatory changes in different jurisdictions. The rise of AI and other sophisticated attacks doesn’t make it easy for companies to stay ahead of fraudsters.
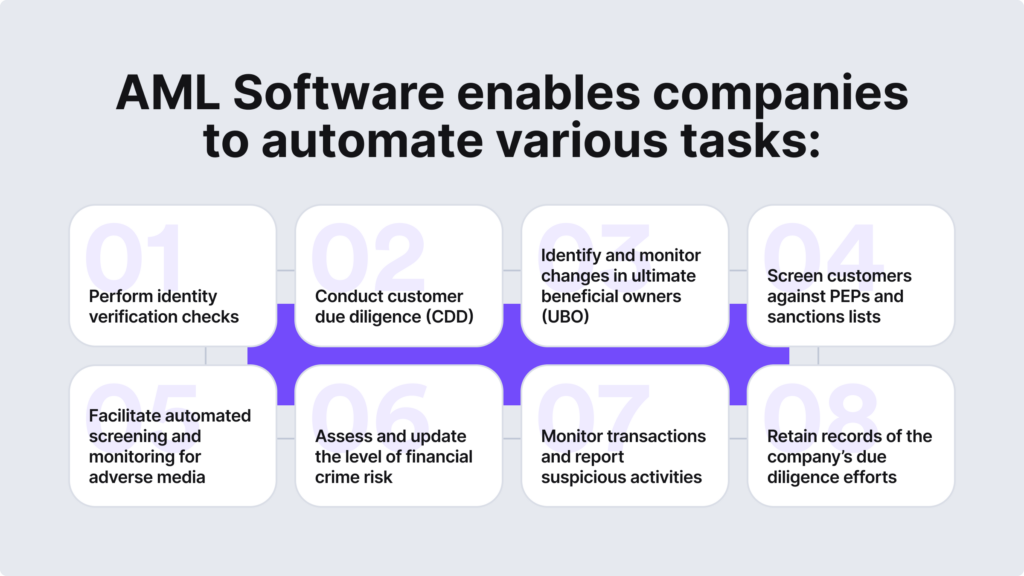
In essence, it’s crucial to verify user identities and monitor for any suspicious activity during onboarding and throughout the whole customer journey in order to keep up with proper fraud detection practices.
Examples of AML Automation Solutions for Effective Fraud Detection
Automated AML solutions help solve the mentioned challenges and ensure proper AML fraud detection. For example:
- Identity verification
- Business verification
- PEPs and sanctions screening
- Watchlist screening
- Adverse media screening
- Customer risk assessment
- Transaction monitoring
To achieve this goal, the AML software should have AML and anti-fraud benchmarks, providing real-time alerts and helping companies ensure efficient case resolution. Additionally, internal employees and all compliance specialists should be aware of the key AML red flags and receive training.
Want to learn more about AML fraud and how to actually detect it without disrupting the user experience and putting a burden on your staff?
iDenfy has many custom rule options and AML automation solutions that can be white-labeled to your unique case. Get a free hands-on experience here.




